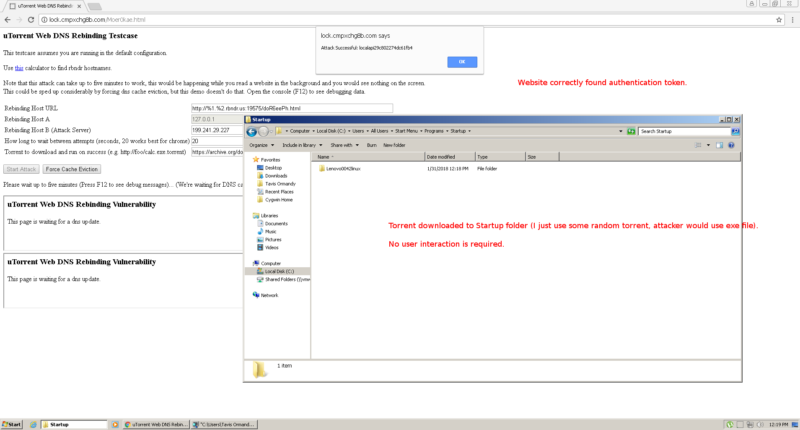
/ A screenshot of one in every of the uTorrent PoC exploits in motion.
Two variations of uTorrent, one in every of the Cyber web’s most broadly dilapidated BitTorrent apps, are inclined to a kind of easy-to-exploit vulnerabilities that allow attackers to enact code, receive entry to downloaded files, and hear in on download histories, a Google Challenge Zero researcher acknowledged. uTorrent builders are within the technique of rolling out fixes for both the uTorrent desktop app for Home windows and the newer uTorrent Web product.
The vulnerabilities, in accordance to Challenge Zero, assemble it doubtless for any web put a user visits to management key functions in both the uTorrent desktop app for Home windows and in uTorrent Web, a replace for desktop BitTorrent apps that uses a web interface and is managed by a browser. Essentially the most exciting threat is posed by malicious sites that will perhaps exploit the flaw to download malicious code into the Home windows startup folder, where it can perhaps perhaps be automatically bustle the subsequent time the laptop boots up. Any put a user visits can additionally receive entry to downloaded files and browse download histories.
In an email sent late Tuesday afternoon, Dave Rees, VP of Engineering at BitTorrent, the developer of the uTorrent apps, acknowledged the flaw has been fixed in a beta birth of the uTorrent Home windows desktop app, nonetheless has no longer but been dropped at users who absorb already obtained the production model of the app set apart in. The fixed model, uTorrent/BitTorrent three.5.three.44352, is available right here for download and can very properly be automatically pushed out to users within the arrival days. In a separate email sent Tuesday evening, Rees acknowledged uTorrent Web had additionally been patched. « We highly aid all uTorrent Web clients to interchange to the latest available build 0.12.0.502 available on our web put and additionally through the in-utility replace notification, » he wrote.
Earlier Tuesday, Challenge Zero researcher Tavis Ormandy warned the failings remained unfixed in uTorrent Web. Rees’s later email indicated that’s no longer the case.
Ormandy’s proof-of-thought exploits consist of this one for uTorrent Web and this one and this one for uTorrent desktop. They utilize a approach identified as area title machine rebinding to assemble an untrusted Cyber web area resolve to the local IP address of the laptop working a inclined uTorrent app. Ormandy’s exploit then funnels malicious instructions through the area to receive them to enact on the laptop. Final month, the researcher demonstrated same serious vulnerabilities within the Transmission BitTorrent app.
Neither Ormandy nor Rees integrated any mitigation advice for inclined uTorrent variations. Other folks who absorb either the uTorrent desktop app for Home windows or uTorrent Web set apart in could perhaps absorb to promptly discontinuance using them until updating to a model that fixes these serious vulnerabilities.

Commentaires récents