Makers of the Telegram instant messenger own mounted a extreme vulnerability that hackers were actively exploiting to set up malware on customers’ computers, researchers said Tuesday.
The flaw, which resided in the Home windows version of the messaging app, allowed attackers to disguise the names of connected files, researchers from safety agency Kaspersky Lab said in a weblog post. By the verbalize of the textual thunder material-formatting traditional identified as Unicode, attackers were in a situation to motive characters in file names to seem from correct to left, as a substitute of the left-to-correct allege that is usual for plenty of Western languages.
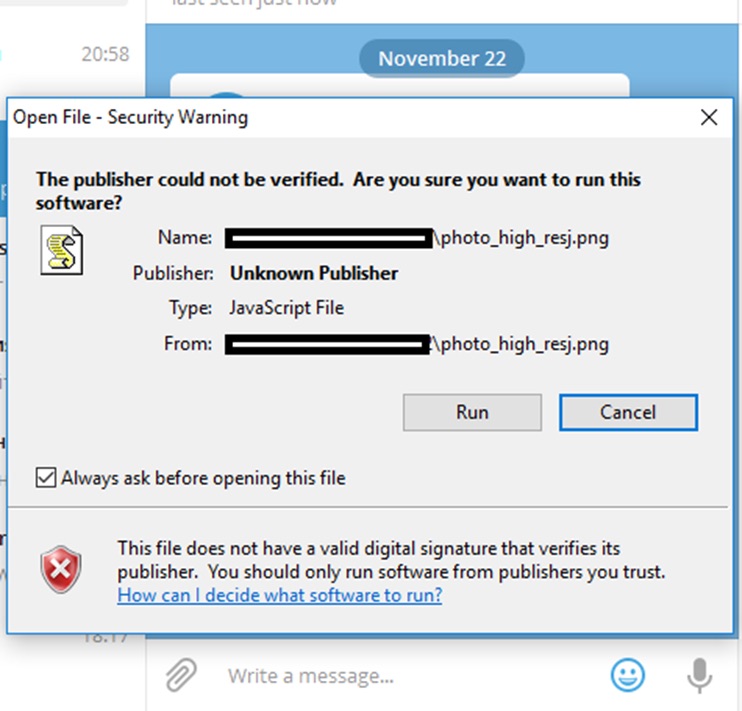
The technique labored by the verbalize of the actual Unicode formatting *U+202E* which causes textual thunder material strings following it to be displayed from correct to left. As a result, Telegram for Home windows transformed files with names reminiscent of « photo_high_regnp.js » to « photo_high_resj.png, » giving the appears to be like to be to be like they were benign image files as a substitute of files that done code.
Malware that makes verbalize of correct-to-left formatting dates relief to as a minimal 2009. four years previously, the pleasant-to-left Unicode trick made a reappearance with malware that targeted computers working both Home windows and macOS.
Kaspersky Lab said hackers with ties to Russian crime gangs were exploiting the Telegram vulnerability to set up two forms of malware on prone computers. One form of malware acted as a power backdoor that gave the attackers total regulate over the compromised computer. The replacement malware mined cryptocurrency. It will not be obvious when Telegram mounted the vulnerability. To be exploited, targets would own to click on by a Home windows warning the same to the one pictured above. Kaspersky Lab said the flaw affected finest the Home windows version of the app.

Commentaires récents