
A rapidly-lively botnet that regarded over the weekend has already infected thousands of Android devices with presumably adverse malware that mines digital money on behalf of the unknown attackers, researchers said.
The beforehand unseen malware using the botnet has worm-like capabilities that allow it to unfold with itsy-bitsy or no particular person interplay required, researchers with Chinese language security firm Netlab wrote in a weblog put up published Sunday. Once infected, Android phones and TV containers scan networks for various devices that maintain Web port 5555 beginning. Port 5555 is most incessantly closed, nonetheless a developer machine is named the Android Debug Bridge opens the port to assassinate a series of diagnostic assessments. Netlab’s laboratory used to be scanned by infected devices from 2,750 unfamiliar IPs within the first 24 hours the botnet grew to develop into energetic, a figure that led researchers to attain that the malware is amazingly rapidly lively.
« General, we maintain there’s a brand new and energetic worm concentrating on Android programs’ ADB debug interface spreading, and this worm has presumably infected greater than 5,000 devices in ethical 24 hours, » Netlab researchers wrote. « These infected devices are actively searching for to unfold malicious code. »
The researchers said they had been withholding some info about the devices which could per chance be getting infected, presumably to compose it harder for copycat attackers to exhaust the same underlying weak point or vulnerability.
Once infected, devices are saddled with an app that causes them to mine the digital coin is named Monero. It be no longer clear what actual pause this mining has on the devices. In previous circumstances, nevertheless, Monero mining apps are so aggressive they physically fret the Android devices running them.
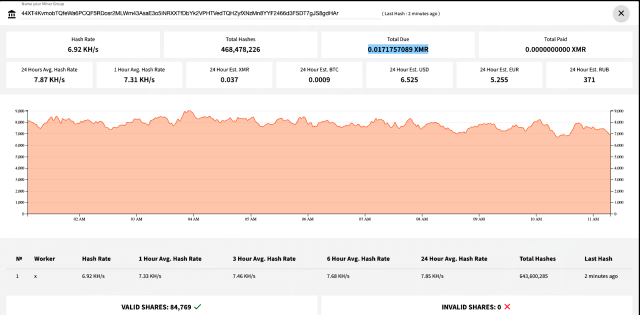
Files returned by Monero Hash Vault—the mining pool the malicious apps exhaust to generate the digital coin—confirmed the attackers maintain a 24-hour moderate payment of seven,880 hashes per 2nd. That is a relatively itsy-bitsy quantity. To this point, the attackers maintain generated zero.0171757089 XMR, which at contemporary costs is payment about $Three.
It be no longer but clear precisely how devices are getting infected. As renowned earlier, Netlab researchers are withholding some particulars, nonetheless they did provide one probably clue after they said one of the an infection code depends on Mirai, the malware that compromises routers and various Web-of-Things devices by guessing default administrator passwords.


Commentaires récents