/ This phishing message feeble Google’s link-shortening provider, allowing researchers to learned little print about doable targets.
Researchers acknowledged Chinese intelligence officers are in the help of practically a decade’s price of network intrusions that recount favorable malware to penetrate tool and gaming companies in the US, Europe, Russia, and in other locations. The hackers indulge in struck as recently as March in a advertising and marketing and marketing campaign that feeble phishing emails in an try and get entry to corporate-sensitive Office 365 and Gmail accounts. Within the assignment, they made serious operational security errors that printed key data about their targets and imaginable space.
Researchers from masses of security organizations indulge in feeble quite a few names to set up accountability for the hacks, including LEAD, BARIUM, Adversarial Panda, GREF, PassCV, Axiom, and Winnti. In many cases, the researchers assumed the teams had been definite and unaffiliated. Based totally on a 49-page story printed Thursday, the general assaults are the work of Chinese govt’s intelligence apparatus, which the story’s authors dub the Winnti Umbrella. Researchers from 401TRG, the threat analysis and diagnosis team at security firm ProtectWise, basically basically based mostly the attribution on general network infrastructure, tactics, tactics, and procedures feeble in the assaults to boot to operational security errors that printed the imaginable space of person individuals.
A decade of hacks
Assaults connected to Winnti Umbrella were energetic since at the least 2009 and presumably date help to 2007. In 2013, antivirus firm Kaspersky Lab reported that hackers the usage of computers with Chinese and Korean language configurations feeble a backdoor dubbed Winnti to infect bigger than 30 on-line on-line sport companies over the outdated four years. The attackers feeble their unauthorized get entry to to map digital certificates that had been later exploited to signal malware feeble in campaigns focusing on various industries and political activists.
Also in 2013, security firm Symantec reported on a hacking neighborhood dubbed Hidden Linx that used to be in the help of assaults on bigger than A hundred organizations, including the excessive-profile 2012 intrusion that stole the crypto key from Bit9 and feeble it to infect at the least three of the safety firm’s customers.
In later years, security organizations Novetta, Cylance, Pattern Micro, Citizen Lab, and ProtectWise issued experiences on masses of Winnti Umbrella campaigns. One advertising and marketing and marketing campaign enthusiastic the excessive-profile network breaches that hit Google and 34 various companies in 2010.
« The motive of this story is to map public previously unreported hyperlinks that exist between a series of Chinese direct intelligence operations, » The ProtectWise researchers wrote. « These operations and the teams that construct them are all linked to the Winnti Umbrella and efficiency below the Chinese direct intelligence apparatus. »
The researchers persevered:
Contained in this story are little print about previously unknown assaults against organizations and the plan these assaults are linked to the evolution of the Chinese intelligence apparatus over the final decade. Based totally on our findings, assaults against smaller organizations function with the aim of finding and exfiltrating code-signing certificates to signal malware for recount in assaults against bigger-price targets. Our foremost telemetry contains months to years of corpulent-fidelity network traffic captures. This dataset allowed us to analyze energetic compromises at multiple organizations and bustle detections against the historical dataset, allowing us to construct a colossal amount of exterior infrastructure diagnosis.
The teams incessantly recount phishing to manufacture entry exact into a purpose’s network. In earlier assaults, the affiliated teams then feeble the preliminary compromise to set up a custom backdoor. More recently, the teams indulge in adopted so-called residing-off-the-land an infection tactics, which depend upon a purpose’s possess popular get entry to systems or draw administration tools to spread and preserve unauthorized get entry to.
The domains feeble to bring malware and provide an explanation for regulate over infected machines incessantly overlap as effectively. The attackers on the general depend upon TLS encryption to hide malware supply and provide an explanation for-and-regulate traffic. In fresh times, the teams depend upon Let’s Encrypt to signal TLS certificates.
Phishing minnows to expend whales
The teams hack smaller organizations in the gaming and skills industries and then recount their code-signing certificates and various property to compromise predominant targets, that are basically political. Most important targets in past campaigns indulge in incorporated Tibetan and Chinese journalists, Uyghur and Tibetan activists, the govt. of Thailand, and grand skills organizations.
Closing August, Kaspersky Lab reported that network-administration tools equipped by tool developer NetSarang of South Korea had been secretly poisoned with a backdoor that gave attackers complete regulate over the servers NetSarang customers. The backdoor, which Kaspersky Lab dubbed ShadowPad, had similarities to the Winnti backdoor and one other fragment of malware also connected to Winnti called PlugX.
Kaspersky acknowledged it stumbled on ShadowPad thru a referral from a associate in the monetary industry that seen a laptop feeble to construct transactions used to be making suspicious domain-name search for requests. At the time, NetSarang tools had been feeble by a complete bunch of banks, energy companies, and pharmaceutical manufacturers.
Opsec errors
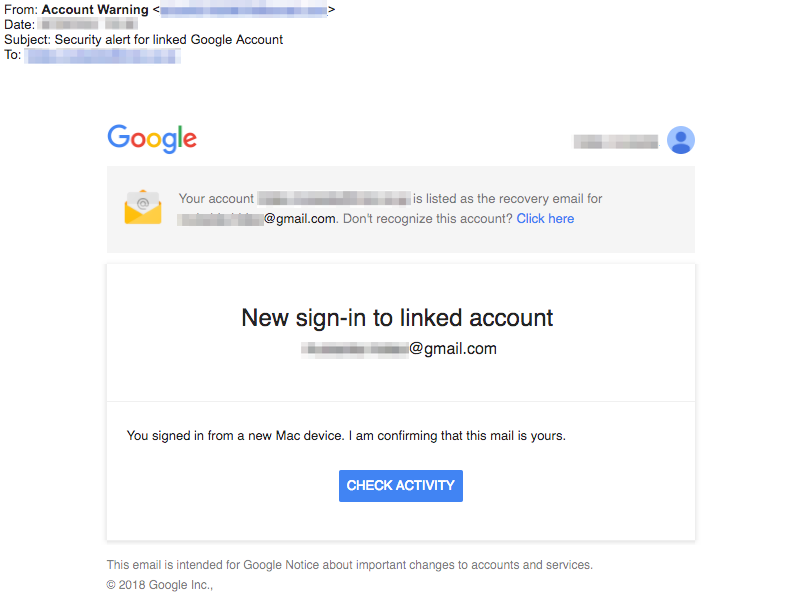
ProtectWise acknowledged since the foundation of the 365 days, individuals of Winnti indulge in waged phishing assaults that try and trick IT workers in masses of organizations to present over login credentials for accounts on cloud products and companies a lot like Office 365 and G Suite. One advertising and marketing and marketing campaign that ran for eight days starting up on March 20 feeble Google’s goo.gl link-shortening provider allowed ProtectWise to recount Google’s analytics provider to safe key little print. An image of the message appears to be like at the pause of this post.
The provider showed that the link used to be created on February 23, some three weeks ahead of the advertising and marketing and marketing campaign went reside. It also showed the malicious phishing link had been clicked a complete of fifty six times: 29 times from Japan, 15 times from the US, twice from India, and as soon as from Russia. Chrome browsers clicked on the link 33 times, and 23 clicks came from Safari customers. Thirty clicks came from Windows computers, and 26 from macOS hosts.
Attackers who received get entry to to targets’ cloud products and companies sought inner network documentation and tools for remotely accessing corporate networks. Attackers who prevail in most cases feeble automatic processes to scan inner networks for originate ports eighty, 139, 445, 6379, 8080, 20022, and 30304. Those ports demonstrate an interest in Internet, file storage products and companies, and purchasers that recount the Ethereum digital currency.
More incessantly than not, the attackers recount their provide an explanation for-and-regulate servers to hide their factual IP addresses. In a few instances, alternatively, the intruders mistakenly accessed the infected machines without such proxies. In all those cases, the block of IPs had been 221.216.Zero.Zero/Thirteen, which belongs to the China Unicom Beijing Community in the Xicheng District.
« The attackers grow and be taught to evade detection when imaginable but lack operational security when it involves the reuse of some tooling, » the story concluded. « Living off the land and adaptability to person purpose networks allow them to function with excessive charges of success. Though they’ve infrequently been sloppy, the Winnti umbrella and its connected entities remain a refined and potent threat. »

Commentaires récents