I’ve Correct Launched « Pwned Passwords » V2 With Half of a Billion Passwords for Download
Final August, I launched barely of arrangement internal Possess I Been Pwned (HIBP) I known as Pwned Passwords. This used to be a record of 320 million passwords from a vary of assorted knowledge breaches which organisations could well possibly exhaust to greater give protection to their very grasp systems. How? NIST explains:
When processing requests to set and alternate memorized secrets, verifiers SHALL compare the seemingly secrets against a record that contains values known to be continuously-used, anticipated, or compromised.
They then walk on to recommend that passwords « got from outdated breach corpuses » desires to be disallowed and that the service must « relate the subscriber that they’ve to make a name a varied secret ». This makes a range of sense in case you suspect about it: if any individual is signing up to a service with a password that has previously regarded in a knowledge breach, either it’s a long way the the same particular person reusing their passwords (substandard) or two varied those who by mere accident, have chosen exactly the the same password. Really, this implies they doubtlessly both have canines with the the same name or one other non-public attribute they’re naming their passwords after (also substandard).
Now all of this used to be substantial advice from NIST, however they stopped looking providing the one element organisations in actuality have to create all this work: the passwords themselves. This is the explanation I created Pwned Passwords – because of this of there used to be a gap that necessary filling – and let’s face it, I affect have gain admission to to rather a range of them courtesy of working HIBP. So 6 months within the past I launched the service and on the original time, I’m happy to launch model 2 with more passwords, more capabilities and one thing I’m in particular enthusiastic by – more privacy. Here’s what it’s all about:
There is Now 501,636,842 Pwned Passwords
Aid on the V1 launch, I explained how the distinctive knowledge set used to be created from sources equivalent to the Anti Public and Exploit.in combo lists as properly as « a vary of other knowledge sources ». In V2, I’ve expanded that to encompass a bunch of knowledge sources alongside with 2 most necessary ones:
- The 711 million narrative Onliner Spambot dump. This used to be a lot of labor to parse various knowledge formats and whereas you occur to read the comments on that blog put up, it’s seemingly you’ll maybe maybe gain a contrivance of how powerful of us wanted this (and why it used to be problematic).
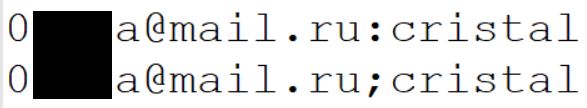
- The 1.4B sure textual exclaim credentials from the « unlit web ». This recordsdata resulted in many fully overblown recordsdata reviews (and contributed to my « unlit web » FUD blog put up last week), however it indubitably did support as a precious reference for V2. This recordsdata also had a bunch of integrity problems which intended the right kind number used to be considerably less. As an illustration, the right kind same username and password pairs acting with varied delimiters:
There is also a heap of other separate sources there the set passwords had been accessible in evil textual exclaim. As with V1, I’m no longer going to name them here, suffice to advise it’s a long way a big sequence from many more breaches than I used within the distinctive model. It be taken a heap of effort to parse by these however it indubitably’s helped manufacture that record up to previous the half of billion label which is a necessary quantity of knowledge. From a defensive standpoint, here is suitable – more knowledge ability more potential to block unhealthy passwords.
However I have not appropriate added knowledge, I’ve also removed some. Let me uncover why and to delivery with, let’s affect a like a flash recap on the explanation for hashing them.
They’re Still SHA-1 Hashed, However with Some Junk Eradicated
When I launched V1, I explained why I SHA-1 hashed them:
It’s no longer in actuality important that SHA1 is a like a flash algorithm tainted for storing your customers’ passwords with because of this of that’s no longer what we’re doing here, it’s simply about making sure the provision passwords are no longer true now visible.
That is mild A hundred% perfect as of on the original time. There are indubitably those who don’t have confidence this methodology; they claim that either the knowledge is without disaster discoverable enough on-line anyway or conversely, that SHA-1 is an insufficiently sturdy algorithm for password storage. They’re true, too – on both capabilities – however that’s no longer what here is about. The total point is to create particular that any non-public recordsdata within the provision knowledge is obfuscated such that it requires a concerted effort to clutch the protection, however that the knowledge is mild usable for its intended purposes. SHA-1 has performed that in V1 and I’m mild confident enough within the model to exhaust the the same methodology in V2.
Even handed one of many issues that did shock me barely of in V1 used to be the effort some of us went to in show to crack the passwords. I used to be taken aback essentially for the explanation that overwhelming majority of those passwords had been already accessible within the sure by the 2 combo lists I talked about earlier anyway, so why effort? Correct download the (without disaster discoverable) lists! The penny that later dropped used to be that it offered a topic topic – and of us love challenges!
One upside from of us cracking the passwords for fun used to be that CynoSure Top managed to name a bunch of junk. Attributable to the integrity of the provision knowledge being barely patchy in locations, there had been entries equivalent to the following.
- $HEX[e3eeeb]
- 6dcc978317511fd8
-
Pointless to reveal, it’s conceivable of us in actuality used these strings as passwords however making exhaust of barely of Occam’s Razor means that it’s simply parsing factors upstream of this recordsdata set. In total, CynoSure Top identified 3,472,226 junk records which I’ve removed in V2. (Incidentally, these are the the same guys that came upon the shortcomings in Ashley Madison’s password storage methodology assist in 2015 – they affect fantastic work!)
Frankly although, there is minute point in eradicating about one million junk strings. It lowered the general knowledge dimension of V2 by zero.sixty 9% and as opposed to the shrimp allotment of extra bytes added to the set, it makes no helpful distinction to how the knowledge is used. On that point and by manner of extraneous records, I desire to be in actuality sure about the following:
This record is no longer most involving – it’s a long way no longer intended to be most involving – and there will be some junk because of this of enter knowledge fantastic and a few missing passwords because of this of they weren’t within the provision knowledge units. It be simply intended to be a record of strings that pose an elevated threat if used for passwords and for that reason, it’s enormously fantastic.
Whereas the total decision of records integrated in V2 is important, it also doesn’t uncover the total story and certainly the feedback from V1 used to be that the 320M passwords necessary one thing more: an indicator of appropriate how substandard each and each one in actuality used to be.
Each Password Now Has a Count Next to It
Is the password « abc123 » worse than « acl567 »? Most password strength meters would have in thoughts them the same because of this of mathematically, they’re. However as I’ve said sooner than, password strength indicators support of us create sick-suggested picks and here is a most involving instance of that. They’re both awful passwords – don’t gain me injurious – however a predictable keyboard pattern makes the damaged-down powerful worse and that is now mirrored within the Pwned Passwords knowledge.
Now on the one hand, it’s seemingly you’ll maybe possibly argue that as soon as a password has regarded breached even appropriate as soon as, it’s unfit for future exhaust. It’ll walk into password dictionaries, be tested against the username it used to be subsequent to and for ever and ever more be a ancient decision in spite of the set it looks within the prolonged bustle. However, I got a range of feedback from V1 alongside the traces of « simply blocking off 320M passwords is a usability nightmare ». Blocking half of 1000000000, even more so.
In V2, every single password has a depend subsequent to it. What this implies is that subsequent to « abc123 » you are going to survey 2,670,319 – that’s what number of instances it regarded in my knowledge sources. Clearly with a number that high, it regarded many instances over within the the same sources because of this of many folks chose the the same password. The password « acl567 », alternatively, only regarded as soon as. Having visibility to the prevalence ability, to illustrate, it’s seemingly you’ll maybe possibly outright block every password that’s regarded A hundred instances or more and force the user to gain one other one (there are 1,858,690 of those within the knowledge set), strongly recommend they occupy a varied password the set it’s regarded between 20 and Ninety 9 instances (there is an extra 9,985,150 of those), and merely flag the narrative if it’s within the provision knowledge no longer up to 20 instances. Pointless to reveal, the password « acl567 » can also properly be deemed too ancient by the necessities of the web site even without Pwned Passwords so here is in no contrivance the single take a look at a website must practice.
In total, there had been 3,033,858,815 occurrences of those 501,636,842 distinctive passwords. In other words, on common, each and every password regarded 6 instances across various knowledge breaches. In some instances, the the same password regarded many instances within the one incident – normally thousands of instances – because of this of that’s what number of folks chose the the same rattling password!
Now, having said all that, within the lead-up to the launch of V2 I’ve had of us argue vehemently that they all desires to be blocked or that none of them desires to be blocked or any aggregate in between. That is lower than me, that’s up to whoever makes exhaust of this recordsdata, my job is solely to present of us enough knowledge with a opinion to create suggested choices. My grasp subjective eye on here is that « it depends upon »; varied threat ranges, varied audiences and varied mitigating controls must all element into this decision.
I Have not Included Password Size
One ask that came up about a instances used to be to encompass a dimension attribute on each and every password hash. This fashion, those using the knowledge could well possibly exclude passwords from the distinctive knowledge set that fall beneath their minimal password dimension necessities. The thinking there being that it would minimize the knowledge dimension they’re attempting by thus realising some efficiency (and possibly monetary) positive factors. However there are a range of reasons why this within the spoil didn’t create sense:
The first is that from the attitude of shielding the provision knowledge (take into accout, it contains PII in locations), explicitly specifying the scale enormously reduces the effort required to crack the passwords. Yes, I know I said earlier that the hashing methodology wasn’t intended to be extremely resilient, however providing a dimension could well possibly be greatly detrimental to the protection that SHA-1 does provide.
Then, I in actual fact got barely scientific about it and looked at what minimal dimension password web sites required. Really, that’s why I wrote the half on minimal dimension by the arena’s high sites a pair of weeks assist; I desired to do stressful numbers on it. eleven of the 15 sites I referred to had a minimal dimension of 6 chars or less. When I then went and looked on the knowledge set I used to be using, as opposed to passwords of no longer up to six chars would have only lowered the set by no longer up to 1% Rather than anything below 8 chars would have lowered it by appropriate below sixteen%. They’re very shrimp numbers.
Then there is the overhead required to host and search this recordsdata, that’s the overhead those organisations who exhaust this could maybe maybe maybe incur. It desires to be very shut to nothing with the total half of billion knowledge set. Chuck it in a storage grasp love Azure Table Storage and likewise you take a survey at single digit greenbacks per month with single digit millisecond lookup instances. There is no longer any want for this to be to any extent extra complex than that.
So in transient, it do the protection of the hashing at bigger threat, there used to be minute or free of fee won and it’s easy to place into effect this in a contrivance that’s speedily and cheap anyway. Some of us will disagree, however a range of belief went into this and I’m confident that the conclusion used to be essentially the most involving one.
Downloading the Recordsdata
And now to the pointy bit – downloading the knowledge. As with V1, there is one substantial 7z archive it’s seemingly you’ll maybe possibly possibly also walk and pull down true now from the Pwned Passwords page on HIBP. Also as sooner than, it’s accessible by inform download from the web site or by torrent. I desire to strongly support you to raise it by the torrent, let me uncover why:
The underlying storage grasp for this recordsdata is Azure Blob storage. If I used to be to support the file straight from there, I’d cop a very hefty knowledge bill. Cloudflare came to rescue in V1 and gave me a free belief that enabled a file of that dimension to be cached as their edge nodes. The affect of that on my bill used to be huge:
Yet some other huge thanks to @Cloudflare for supporting the @haveibeenpwned Pwned Passwords, appropriate did the arithmetic on how powerful it saved me – whoa! pic.twitter.com/70kki5Uw7o
— Troy Hunt (@troyhunt) August 15, 2017
Have faith the discussion I’d be having with my necessary other if it wasn’t for Cloudflare’s increase! And that used to be sooner than one other 6 months’ price of downloads too. Cloudflare could well possibly want given me the service for free, however they mild have to pay for bandwidth so I’d dangle to quiz on your increase in pulling the knowledge down by torrents in its set of from the inform download hyperlink. To that halt, the UI actively encourages you to defend the torrent:

Whenever it’s seemingly you’ll maybe possibly possibly also’t defend the torrent (and I’m wide awake there are, to illustrate, corporate environments the set torrents are blocked), then download it inform however affect your bit to support me out by supporting the of us supporting me the set it’s seemingly you’ll maybe possibly possibly also. As with V1, the torrent file is served straight from HIBP’s Blob Storage and likewise yow will detect a SHA-1 hash of the Pwned Passwords file subsequent to it so that it’s seemingly you’ll maybe possibly possibly also take a look at integrity whereas you occur to’re so inclined.
In advise that’s the download – walk forth and affect appropriate issues with it! Now for one thing else wintry and that is the on-line search.
Querying the Recordsdata Online
In V1, I stood up an on-line search arrangement the set it’s seemingly you’ll maybe possibly walk in a password and survey if it regarded within the knowledge set. That sat on high of an API which I also made accessible for unbiased consumption must of us dangle to exhaust it. And tons folks did exhaust it. Really, among the crucial entrants to my competition to defend a Lenovo computer leveraged that proper endpoint including the winner of the competition, sixteen,one year-outdated Félix Giffard. He created PasswordSecurity.recordsdata which straight consumes the Pwned Passwords API by the client facet:

Getting assist to the on-line search, being attentive to no longer looking to send the injurious message to of us, true now sooner than the quest field I do a extremely sure, very bold message: « Attain no longer send any password you actively exhaust to a third-celebration service – even this one! »
However of us don’t continuously read these objects. The service got a heap of press and thousands and thousands of of us descended on the net site to take a look at their passwords. At the least I spend it used to be their passwords, I indubitably don’t log those searches however in step with the knowledge articles and social media commentary, yeah, it would had been a heap of proper passwords. And I’m in actuality okay with that – let me uncover:
As powerful as I manufacture no longer desire to support of us to walk their proper password(s) into random third-celebration sites, I will guarantee that a big decision of of us got a undeniable hit and then changed their security hygiene because of this. Even handed one of essentially the most involving issues that’s resonated with me in working HIBP is how powerful affect it’s had on altering user behaviour. Seeing either your electronic mail tackle or your password pwned has a contrivance of constructing of us reconsider some of their security choices.
The gain search works virtually identically to V1 albeit with the depend of the password now represented too:

Swish easy stuff and for essentially the most half, also dazzling acquainted. However there is one in actuality important – and in actuality wintry – distinction. Let me uncover:
Cloudflare, Privacy and okay-Anonymity
In what proved to be very fortuitous timing, Junade Ali from Cloudflare reached out to me last month with an belief. They desired to manufacture a tool to search by Pwned Passwords V1 however to electrify so in a contrivance that allowed exterior parties to exhaust it and defend anonymity. You survey, the disaster with my present implementation used to be that whereas it’s seemingly you’ll maybe possibly pass appropriate a SHA-1 hash of the password, if it returned a success and I used to be to raise that and reverse it assist to the sure (which I could well possibly without disaster affect because of this of I created the hashes within the first quandary!) I’d know the password. That made the service stressful to utter sending proper passwords to.
Junade’s belief used to be varied although; he proposed using a mathematical property known as okay-anonymity and throughout the scope of Pwned Passwords, it in actuality works love this: imagine whereas you occur to desired to take a look at whether or no longer the password « P@ssw0rd » exists within the knowledge set. (Incidentally, the hackers have worked out of us affect stuff love this. I know, it sucks. They’re onto us.) The SHA-1 hash of that string is « 21BD12DC183F740EE76F27B78EB39C8AD972A757 » so what we will affect is lift appropriate the first 5 characters, in this case which ability that « 21BD1 ». That will get sent to the Pwned Passwords API and it responds with 475 hash suffixes (that is every thing after « 21BD1 ») and a depend of what number of instances the distinctive password has been viewed. As an illustration:
- (21BD1) 0018A45C4D1DEF81644B54AB7F969B88D65:1 (password « lauragpe »)
- (21BD1) 00D4F6E8FA6EECAD2A3AA415EEC418D38EC:2 (password « alexguo029 »)
- (21BD1) 011053FD0102E94D6AE2F8B83D76FAF94F6:1 (password « BDnd9102 »)
- (21BD1) 012A7CA357541F0AC487871FEEC1891C49C:2 (password « melobie »)
- (21BD1) 0136E006E24E7D152139815FB0FC6A50B15:2 (password « quvekyny »)
- …
I added the prefix in brackets beforehand and the provision passwords in brackets afterwards simply as an instance what we’re doing here; they’re all appropriate varied strings that hash the general manner down to values with the the same first 5 characters. In other words, they’re all throughout the the same « vary » and likewise you are going to survey that length of time referenced more later on. Using this model, any individual attempting the knowledge set appropriate will get assist the hash suffixes and counts (every thing in bold after the first 5 chars) and in addition they’ll then survey if every thing after the first 5 chars of their hash matches any of the returned strings. Now perceive that up to now as I’m concerned, the partial hash I used to be sent will likely be any person of 475 varied conceivable values. Or it could maybe maybe possibly be one thing fully varied, I simply do no longer know and therein lies the anonymity cost.
For the sake of point of view, here are some stats on what this implies for the knowledge internal Pwned Passwords:
- Every hash prefix from 00000 to FFFFF is populated with knowledge (sixteen^5 combos)
- The frequent decision of hashes returned is 478
- The smallest is 381 (hash prefixes « E0812 » and « E613D »)
- The greatest is 584 (hash prefixes « 00000 » and « 4A4E8 »)
Junade has written a substantial half that’s appropriate long previous are living on Cloudflare’s blog titled Validating Leaked Passwords with okay-Anonymity and he goes into more depth in that half. As he explains, there are other cryptographic approaches which could well possibly also tackle the will for anonymity (to illustrate, non-public set intersections), however no longer with the benefit and level of simplicity Junade proposed. I cherished it so powerful that I offered to manufacture and bustle it as a service out of HIBP. Junade (and Cloudflare) belief that used to be a substantial belief so they offered to point of us over to the HIBP model in its set of manufacture out one thing fully separate. That is a partnership I’m enormously happy with I like their self assurance in my working it.
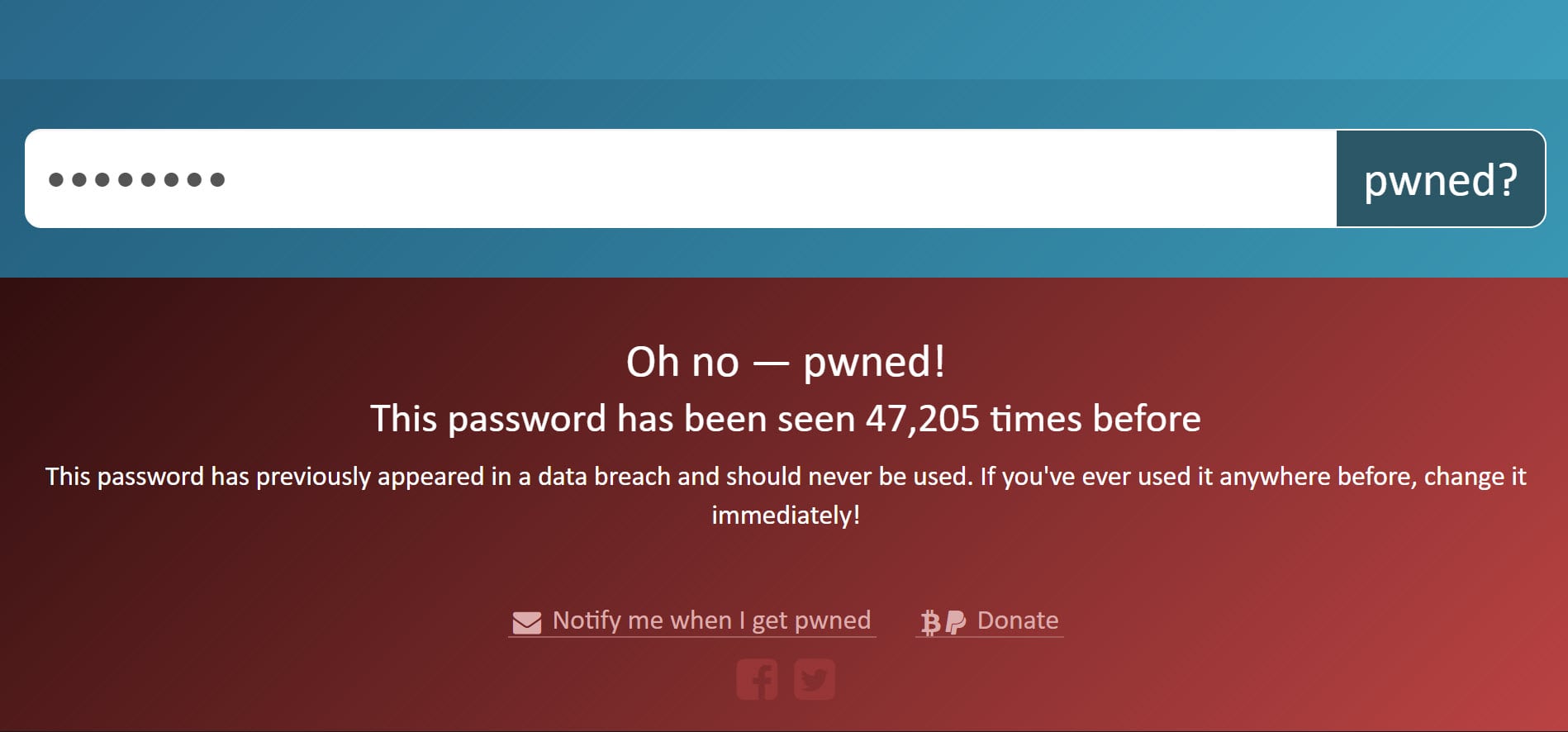
This model of anonymity is what now sits within the assist of the on-line search arrangement. You have to maybe maybe maybe survey it in action by attempting a stare for « P@ssw0rd » which could return the show cloak cloak within the outdated image. If we tumble down and elevate a survey on the dev tools, here is the right kind ask that’s been made:
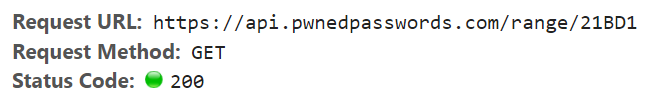
The password has been hashed client facet and appropriate the first 5 characters passed to the API (I will discuss more about the mechanics of that at the moment). Here’s what then comes assist within the response:
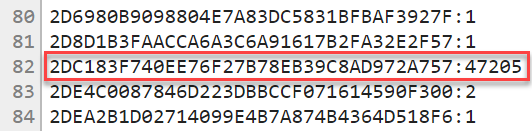
As talked about earlier, there are 475 hashes starting with « 21BD1 », however only 1 which goes the remainder of the hash for « P@ssw0rd » and that narrative implies that the password has previously been viewed Forty seven,205 instances. And that’s the explanation it – that’s what I’ve performed with Cloudflare’s increase and that is what now we have performed together to give protection to anonymity and create the service accessible to every person. Let me now discuss about the manner to exhaust the API.
Drinking the API (and the Mechanics At the assist of the Fluctuate Search)
The original API documentation on HIBP has been updated so that it’s seemingly you’ll maybe possibly possibly also walk there for the total implementation shrimp print. There are about a issues namely I desire to name out although:
Firstly, you are going to survey that I’m serving this API from a varied domain to the other HIBP APIs and certainly from V1 of the Pwned Passwords service. For V2, I’ve stood up an Azure Characteristic on the api.pwnedpasswords.com domain which will get the API out of the HIBP online page and working on serverless infrastructure in its set. I’ve written about Azure Capabilities within the previous and in addition they’re an endless manner of constructing a extremely scalable, resilient « code as a service » structure. It ensures that load comes off the HIBP online page and that I will scale the Pwned Passwords service infinitely, albeit with a line straight to my pockets! It be also given me the flexibility to electrify issues love perfect off a bunch of excessive headers equivalent to the exclaim security coverage HIBP makes exhaust of (that’s of no exhaust to a lone API endpoint).
Secondly, the original API (that many folks have created dependencies on!) mild works appropriate elegant. It also capabilities to the storage repository for V2 of the password set so it’s now attempting by the paunchy half of billion records. I will leave this working for the foreseeable future, however whereas you occur to can also very properly be using it then I’d dangle you roll over to the endpoint on api.pwnedpasswords.com for the reasons talked about above, and for these other reasons:
Whenever you had been using the distinctive API by HTTP GET, rolling over to the unique one changes completely nothing on your implementation as opposed to the URL which could look love this:
GET https://api.pwnedpasswords.com/pwnedpassword/{password}It’ll mild return HTTP 200 when a password is came upon and 404 when it’s a long way no longer. The one distinction (and this need to no longer rupture any present usages), is that the 200 response now also contains a depend within the body by manner of a single integer:

And as sooner than, it’s seemingly you’ll maybe possibly possibly also continuously pass a hash if most standard:

However, pointless to reveal, now we have appropriate had the anonymity chat and likewise it’s seemingly you’ll maybe possibly have viewed the course for calling that endpoint earlier on. Correct to point it out some other time here, it’s seemingly you’ll maybe possibly possibly also pass the first 5 chars of the hash to this tackle:
https://api.pwnedpasswords.com/vary/{hashPrefix}Which returns a consequence love this:

Endure in thoughts, these are all hash suffixes (followed by a depend) so the paunchy cost of the first hash, to illustrate, is « 21BD10018A45C4D1DEF81644B54AB7F969B88D65 ». Incidentally, enter to the API is no longer case gentle so « 21bd1 » works appropriate as properly as « 21BD1 ». All hash suffixes returned (and certainly those offered within the downloadable knowledge) are uppercase impartial because of this of that’s the default output from SQL Server’s HASHBYTES arrangement (I processed the provision knowledge in a local RDBMS instance).
Unlike the distinctive model, there isn’t any longer any rate-limiting. That used to be a grasp I necessary essentially to give protection to non-public knowledge within the breached account search (i.e. in case you stare on your electronic mail tackle amongst knowledge breaches), however I prolonged it to Pwned Passwords as properly to support give protection to the infrastructure. Now working on serverless Azure Capabilities, I manufacture no longer have that disaster so I’ve dropped it altogether. I’d also dropped model numbers, I will tackle that after I want them that is rarely be for a extremely very prolonged time (if ever).
Now, about a more issues spherical some manufacture choices I’ve made: I’m very wary of the aptitude affect on my pockets of working the service this trend. It be one element to arise V1 that only returned an HTTP response code, used to be rate-restricted and in actuality wasn’t designed to be known as in bulk by a single user (pondering the privacy implications), it’s barely one other to electrify what I’ve performed with V2, especially when each and every search of the vary API returns a range of of records. That « P@ssw0rd » search, to illustrate, returns 9,730 bytes when gzipped (that’s a blinding common dimension) and I’m paying for egress bandwidth out of Azure, the execution of the arrangement and the name to the underlying storage. Tiny portions each time, thoughts you, however I’ve needed to minimize that affect on me up to now as conceivable by a vary of measures.
As an illustration, the tip outcomes of that vary do a question to is no longer a neatly formatted half of JSON, it’s appropriate colon delimited rows. That impacts my potential so that you can add attributes at a later date and dazzling powerful locks within the most fresh model to on the original time’s behaviour, however it indubitably saves on the response dimension. Yes, I know some curly braces and quotes wouldn’t add a range of dimension, however every byte counts when volumes gain substantial.
Additionally, you will survey there is a prolonged max-age on the cache-support watch over header:

Here’s 31 days’ price of cache and the following Cloudflare cache suppose header explains why: by routing by their infrastructure, they’ll aggressively cache these outcomes which ensures no longer only is the response lightning speedily (take into accout, they at the moment have 121 edge nodes spherical the arena so there is one attain you), however that I manufacture no longer do on the monetary hit of of us hammering my foundation. Especially in case it’s seemingly you’ll maybe possibly possibly even have in thoughts the extent to which more than one of us exhaust the the same password, after we’re talking about the vary search the set many varied passwords have the same hash prefixes, there is some necessary benefits to be had from caching. As talked about earlier, there are sixteen^5 varied hash prefixes (1,048,576) throughout the vary of 00000 to FFFFF so that it’s seemingly you’ll maybe possibly possibly also survey how broad usage would earnings enormously from caching across many thousands and thousands of searches. The efficiency distinction on my own when evaluating a cached consequence with a non-cached one makes a compelling argument:

This implies that even though the response is greatly elevated than in V1, if I will assist a ask to the unique API from cache there is in actuality a huge improvement. Here’s a sequence of hits to V1 the set every single time, the ask needed to head the total manner to the muse server, hit the API and then do a question to 320M records:

In show to create aggressive caching seemingly, I’m also only supporting HTTP GET. Now, some of us will lose their minds over this because of this of they’ll reveal « which ability that it goes into logs and likewise you are going to song the passwords being hunted for ». Whenever you’re troubled about me tracking anything, don’t exhaust the service. That is no longer intended to be a flippant assertion, rather a easy acknowledgment that it’s basic to have confidence the operator of the service whereas you occur to’re going to be sending passwords in any shape or invent. Offsetting that’s the total okay-Anonymity field; even whereas you occur to don’t have confidence the service or you suspect logs will likely be leaked and abused (and incidentally, nothing is explicitly logged, they’re transient machine logs at most), the vary search goes a extremely prolonged manner to keeping the provision. Whenever you mild don’t have confidence it, then appropriate download the hashes and host them yourself. No in actuality, that’s the total point of constructing them accessible and in all honesty, if it used to be me constructing on high of those hashes then I’d indubitably be querying my grasp repository of them.
In abstract, whereas you occur to’re using the vary search then you definately gain safety of the provision password properly in contrivance over what I used to be ready to electrify in V1 plus it’s massively sooner if any person else has performed a stare for any password that hashes the general manner down to the the same first 5 characters of SHA-1. Plus, it helps me out an awful lot by manner of maintaining the costs down!
Pwned Passwords in Action
Lastly, I desire to name out a name of examples of the first era of Pwned Passwords in action. My hope is that they encourage others to manufacture on high of this recordsdata set and within the spoil, create a undeniable distinction to web security for every person.
As an illustration, Workbooks.com (they devise CRM instrument, among other issues) explains to customers that a Pwned Password is ancient or has previously regarded in a knowledge breach.
Then there is Colloq (they support you gape conferences) who’ve written up a substantial half with hundreds of efficiency stats about their implementation of the knowledge.
Or are attempting creating an account on Toepoke with a password of « P@ssw0rd » and survey how that goes for you:

safepass.me also picked up the knowledge and wrapped it into an offline commercial Stuffed with life Itemizing filter (plus a free dwelling model).
On the mobile entrance, there is Pwned Slip within the Google Play store which sits on high of the present API.
Here’s All Still Free (and I Still Like Beer!)
Nothing positive factors traction love free issues! Preserving HIBP free to search your tackle (or your entire domain) used to be essentially the most involving element I ever did by manner of constructing it stick. A few months after I launched the service, I stood up a donations page the set it’s seemingly you’ll maybe possibly settle me some beers (or coffee or other issues). It only went up after of us namely requested for it (« howdy reliable service, can I gain you a coffee? ») and I’ve been in actuality happy with the responses to it. As I reveal on the page, it’s more the time commitment that in actual fact costs me (I’m unbiased so whereas I’m constructing one thing love Pwned Passwords, I’m no longer doing one thing else), however there are also costs which will shock you:
Correct burned by $A hundred of mobile knowledge so that I could well possibly manufacture processing Pwned Passwords this weekend. 110kbps on limitless broadband belief or 8,286kbps on 4G at $10/GB. It used to be going to be stressful to gain it are living subsequent week otherwise 🙁
— Troy Hunt (@troyhunt) February 17, 2018
Here’s a form of good « Australianisms » courtesy of the true fact my up-bustle maxes out at about 1.5Mbps (and is then shared across the total issues in my dwelling that send knowledge out). Down-bustle is about 114 however getting anything up is a nightmare. (And for Aussie associates, no, there isn’t any longer any NBN accessible in my dwelling of the Gold Flit yet, however it indubitably sounds as whether it’s a long way no longer a long way off.) And no, here is no longer a solvable disaster by doing every thing within the cloud and there are a range of reasons why that must no longer have worked (I will blog them at a later date).
Whenever you dangle to have to support kick in for these costs and shout me a sympathy coffee or beer(s), it’s mild very powerful most standard!
Closing
Pwned Passwords V2 is now are living! All the issues it’s basic to exhaust them is over on the Pwned Passwords page of HIBP the set it’s seemingly you’ll maybe possibly possibly also take a look at them on-line, learn about the API or appropriate download the total lot. All those units are free, unrestricted and do not even require attribution whereas you occur to don’t desire to create it, appropriate elevate what’s there and walk affect appropriate issues with it 😀
Be taught Extra
(Visité 4 fois, 1 aujourd'hui)

Commentaires récents