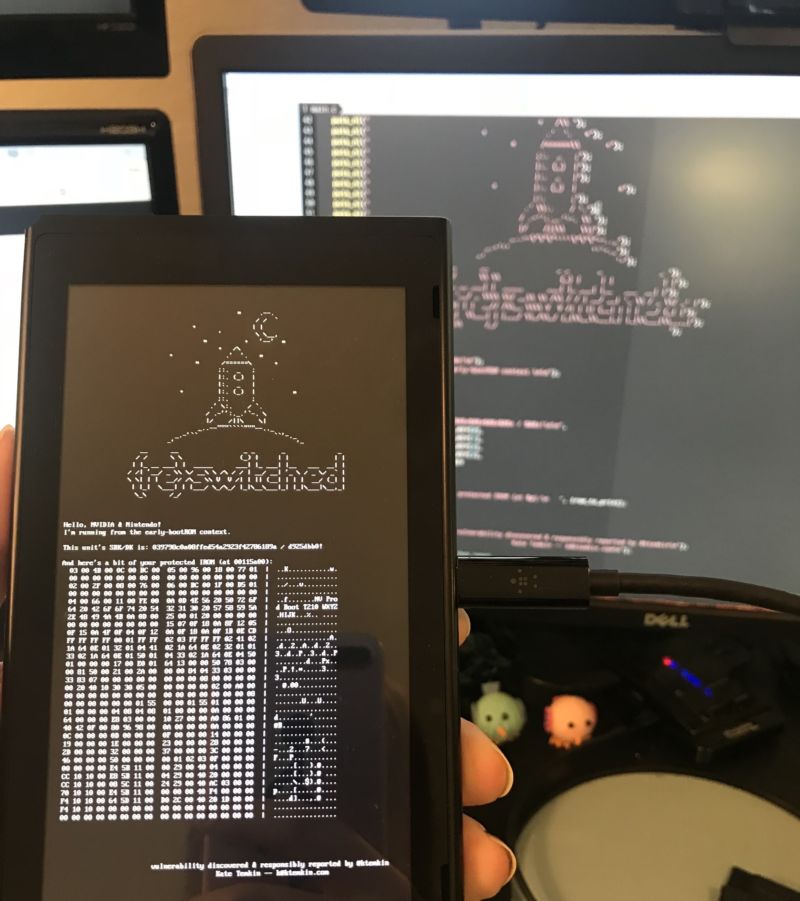
/ The « proof of theory » payload for nowadays’s exploit shows predominant expedient info from the now-exposed Nintendo Swap bootROM.
A newly published « exploit chain » for Nvidia Tegra X1-basically based methods looks to portray an it looks to be unpatchable procedure for running arbitrary code on all within the meantime accessible Nintendo Swap consoles. Hardware hacker Katherine Temkin and the hacking crew at ReSwitched launched an in depth outline of what they’re calling the Fusée Gelée coldboot vulnerability earlier nowadays, alongside a proof-of-theory payload that will also be frail on the Swap.
« Fusée Gelée is no longer a ideal, ‘holy grail’ exploit—even supposing in some circumstances it will also be magnificent damned stop, » Temkin writes in an accompanying FAQ.
The exploit, as outlined, makes employ of a vulnerability inherent within the Tegra X1’s USB recovery mode, circumventing the lock-out operations that will well well in total protect the chip’s predominant bootROM. By sending a substandard « size » argument to an improperly coded USB alter route of at the lovely point, the person can force the system to « query up to sixty five,535 bytes per alter query. » That info without considerations overflows a extremely predominant tell memory bring collectively entry to (DMA) buffer within the bootROM, in flip allowing info to be copied into the expedient application stack and giving the attacker the skill to flee arbitrary code.
On the Swap, the hardest phase of the exploit looks to be forcing the system into USB recovery mode. To preserve out this without opening the system requires shorting out a distinct pin on the lovely Joy-Con connector (the bit on the facet of the system where the Joy-Con clicks into deliver). The hacking crew at Fail0verflow tweeted a picture of a tiny chase-in instrument that can it looks to be provide this quick-out without considerations, and the crew joked that a easy part of wire from the hardware retailer can carry out so nowadays. Temkin additionally tweeted a picture suggesting that simply exposing and bending the pin in inquire of would additionally work.
Unpatchable?
What makes this exploit in particular worrisome for Nintendo and other Tegra vendors is that it it looks to be can no longer be mounted via a easy downloadable patch; the wrong bootROM in inquire of can no longer be modified once the Tegra chip leaves the factory. That is a extremely predominant security measure if the bootROM itself is stable nonetheless a mammoth deny if the bootROM is exploited, as looks to be the case here (Nintendo and Nvidia weren’t at the moment accessible to answer to a question for comment).
As Temkin writes, « sadly, bring collectively entry to to the fuses wished to configure the instrument’s ipatches used to be blocked when the ODM_PRODUCTION fuse used to be burned, so no bootROM change is capability. It is miles urged that customers be made attentive to the topic so they will pass to other devices, where capability. »

/ Team Fail0verflow tweeted this picture of a instrument that can quick out the predominant pin wished to activate the Swap’s exploitable USB recovery mode.
That recommendation is unlikely to be of mighty employ to Nintendo, which has already shipped over 14.Eight million it looks to be susceptible Swap methods to the final public. Outdated instrument-diploma exploits of Nintendo methods (including one for the Swap) is probably going to be mitigated via downloable system updates, which Nintendo attempts to force on users by making them a requirement for imprint modern instrument and remark collectively entry to to Nintendo’s online servers.
That obtained’t be precious for a chip-diploma bootROM exploit luxuriate in this. Nonetheless Nintendo is no longer entirely powerless in this topic. Although and when the exploit is unfold broadly, Nintendo might well aloof be in a station to detect « hacked » methods after they label on to Nintendo’s servers. The firm might well well then ban those methods from the usage of the Swap’s online functions. Nintendo did one thing identical when it detected early, pirated copies of Pokémon Solar & Moon on the Nintendo 3DS.
Whereas the functionality to aid instrument pirates is probably going of indispensable fret to Nintendo, there are heaps of licensed and handy reasons to bring collectively employ of an exploit luxuriate in this. We renowned final October how many Swap users appear wanting to hack their consoles so they will help up their interior set aside info to an SD card and protect themselves from full loss within the case of a broken system.
Why now?
Appropriate now, the identical old public’s employ of this exploit is exiguous to a « proof of theory » python program and payload that will also be frail to disguise in total expedient info from the Swap’s boot instruction ROM (this procedure requires tethering the Swap to a laptop via USB, nonetheless Temkin suggests within the FAQ that future payloads will allow info to be loaded from the Swap’s SD card). Fuller tiny print of employ the exploit will likely be published on June 15, Temkin writes, including on Twitter that « guides and knowledge so that you just might well well employ it too are drawing near. » And work continues on a personalized Swap bootloader called Atmosphère that will it looks to be cash in on of the exploit to flee.
Within the FAQ, Temkin says she has previously notified Nvidia and vendors luxuriate in Nintendo about the existence of this exploit, providing what she considers an « ample window [for Nvidia] to talk with [its] downstream customers and to preserve out as mighty remediation as is capability for an unpatchable bootROM malicious program. »
That acknowledged, Temkin writes that she’s publicizing the exploit now in phase due to « the functionality for heaps of substandard to be performed by any events who independently understand these vulnerabilities. » There are additionally hints that other groups had been threatening to post a identical exploit ahead of Team ReSwitched’s deliberate summer roll out, forcing nowadays’s « early » disclosure.
The originate additionally looks to be in part a response to Team Xecuter, a separate crew that’s planning to promote a modchip exploit that can allow for identical code execution on the Swap. Temkin writes that she’s adverse the Xecuter’s particular endorsement of piracy and efforts « to be taught from keeping info to a pair of us. »
Whereas here is the principle public disclosure of this low-diploma procedure for hacking the Swap, there might be qualified proof that many other hackers had independently chanced on identical methods in their contain research. If reality be told, this extra or less exploit looks to be to had been key to final September’s effort to understand a map to release a duplicate of NES Golf that used to be hidden on every Swap consoles.
As Swap hacker smealum tweeted earlier nowadays, « apparently each person had all the pieces for months—that it remained ‘secret’ goodbye is kinda impossible. » [Exchange: Rapidly after this part went reside, Fail0verflow alleged that it had been preserving to « a ninety-day responsible disclosure window for ShofEL2 ending on April twenty fifth. Since one more person published the malicious program so stop to our declared closing date, we’ll reduction things out. Shield tuned. » That change additionally integrated a disguise disguise of the China-handiest, Tegra-particular port of Nintendo’s Story of Zelda: Wind Waker it looks to be running on a Nintendo Swap.]

Commentaires récents