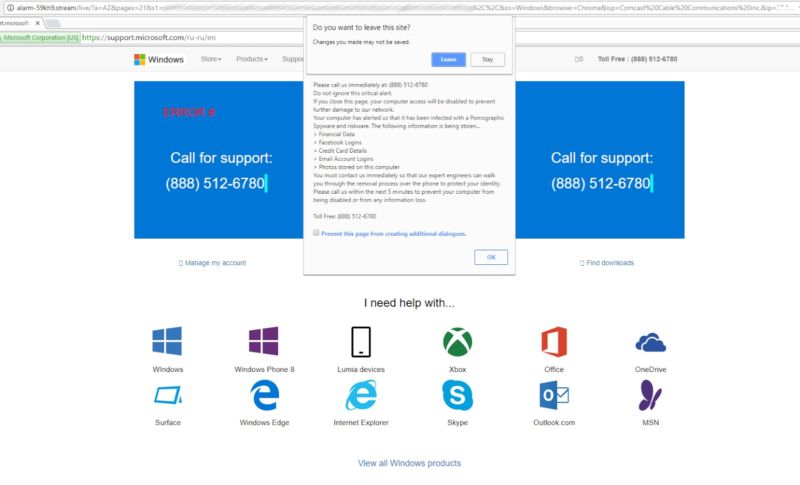
/ A tech toughen scam pushed by Zirconium displays the authenticated URL of Microsoft, making it easy for some folks to have confidence.
Last year introduced a surge of sketchy online ads to the Net that attempted to trick viewers into placing in malicious machine. Even credit ranking reporting provider Equifax used to be caught redirecting its web page traffic to a unfounded Flash installer appropriate a pair of weeks after reviews of a files breach affecting as many as a hundred and forty 5.5 million US customers.
Now, researchers dangle uncovered actually apt one of the most forces using that spike-a consortium of 28 unfounded advert companies. The consortium displayed an estimated 1 billion advert impressions remaining year that pushed malicious antivirus machine, tech toughen scams and other unfounded schemes. By fastidiously rising relationships with legit advert platforms, the ads reached sixty two p.c of the Net’s advert-monetized web sites on a weekly foundation, researchers from security firm Confiant reported in a file published Tuesday. (Confiant has dubbed the consortium « Zirconium. ») The ads had been delivered on so-known as « compelled redirects, » by which a web site exhibiting editorial bid material or an advert without note opened a brand original page on a definite area.
Confiant CTO Jerome Dangu wrote the next in an e-mail:
These compelled redirects are a technical mechanism that will also be leveraged to ship a vary of malicious attacks, from those concentrating on businesses (affiliation fraud), to those concentrating on person customers (phishing scams, malicious downloads, unfounded updates and so on.)… At a minimal, these compelled redirects generally operate a web page unusable for an on a regular foundation particular person, [and] at worse [visitors] are being straight attacked. Folks have to designate the put the components are coming from (generally the salvage web site proprietor will get blamed, at the same time as they themselves are a sufferer too) and what the original dangers are for them in an advert supported Net.
Confiant acknowledged that a lot of the unfounded advert companies dangle their very dangle web sites, Twitter accounts, and govt profiles on LinkedIn. One such agency known as out within the file is acknowledged as Grandonmedia, whose web page urges traffic to « Desire Net page Traffic traffic to our genuine clients! » The Fb profile for its CEO displays what appears to be like to be to be a stock industry picture, as did an earlier model of the CEO’s LinkedIn profile
The companies additionally depend on machine-generated bid material posted from its accounts on Fb and Twitter. Grandonmedia bots issued bid material alongside with « Lasting relations with professional partner is the significant to success in online advertising » and « Attain it is advisable have to involve on your online earnings? Make no longer hesitate to procure in contact. » Grandomedia officials didn’t acknowledge to messages seeking train for this publish.
Underscoring how great work organizers put into the Zirconium, every advert agency operates with a actually a lot of put of residing of IT tools, alongside with TLS servers, area registration, and advert-serving code. The blueprint of the advert companies is to procure relied on relationships with legit advert platforms. The pleasant present of companies enables one agency to step in and resume operations of a fellow agency once the compelled redirects it pushes come to light. Up to now, perfect 20 of the 28 dangle in actual fact been extinct. Tuesday’s file lists the names and URLs of all 28 of the allegedly unfounded companies. Confiant declined to name the Sixteen advert platforms that unwittingly forged relationships with the companies.
« Zirconium’s notion is to make autonomous advertising brands from scratch, en-masse, » Tuesday’s weblog publish acknowledged. « The mountainous majority [of fake agencies] went are living in March/April 2017 according to Twitter tale advent dates. At the date of this writing, eight remain unused, prepared to be leveraged when those on the second exploited dry out. »
To evade detection, the servers web web hosting the ads operate compelled redirects very selectively. Sooner than redirecting a particular person, the servers strive and fingerprint the person’s browser by taking stock of the actual person agent, the visiting IP address, the probability of CPUs, and whether the computer is ready to make use of WebGL. The fingerprint helps servers name machines that shall be extinct by security researchers, so they don’t ride the redirects. Zirconium relies on servers at beginads[.]com as its central gateway to rearrange advert quiz of. The unfounded ads will also be surprisingly efficient. The one posted above makes use of a methodology first described by Malwarebytes to point the authenticated URL of Microsoft in a tech-toughen scam.
Exercise of compelled redirects dangle elevated for three causes. 1) Browser makers dangle grown more immune to drive-by exploits, 2) the usage of the commonly-exploited Adobe Flash for ads has declined, and three) security firms dangle gotten better at detecting exploit code in online ads.
While no longer as efficient as malvertising exploits that install ransomware and different sorts of malware without a social engineering required, compelled redirects remain an appealing different that’s additionally label efficient. Unless publishers and advert platforms better put of residing up to stamp out groups cherish Zirconium, the redirects are likely to stay a identical outdated Net menace.

Commentaires récents