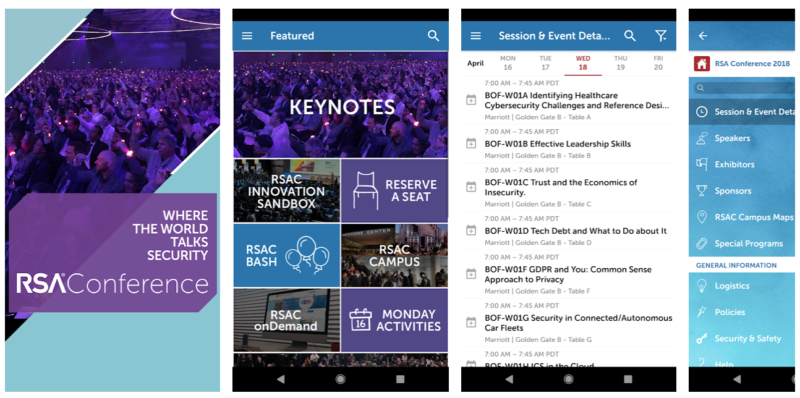
/ Screenshots of the RSA Convention utility from the Google Play Store. The app’s Web interface leaked attendee data when equipped with a token obtained by registering the app.
Google Play Store
A mobile utility built by a 0.33 birthday celebration for the RSA security conference in San Francisco this week used to be chanced on to own a pair of security complications with its possess—including onerous-coded security keys and passwords that allowed a researcher to extract the conference’s attendee listing. The conference organizers acknowledged the vulnerability on Twitter, but they are saying that easiest the first and final names of 114 attendees were exposed.
— RSA Convention (@RSAConference) April 20, 2018
The vulnerability used to be chanced on (at the least publicly) by a security engineer who tweeted discoveries for the length of an examination of the RSA conference mobile app, which used to be developed by Eventbase Technology. Within 4 hours of the disclosure, Eventbase had fixed the details leak—an API call that allowed somebody to make your mind up on up data with attendee data.
For these who attended #RSAC2018 and evaluate your first title there – sorry! 😳pic.twitter.com/YrgZo6jHDu
— svbl (@svblxyz) April 20, 2018
Gaining access to the attendee listing required registering an story for the utility, logging in, and then grabbing a token from an XML file saved by the utility. Since registration for the utility easiest required an email take care of, somebody who could perchance perchance dump the files from their Android arrangement could perchance perchance produce the token and then insert it into a Web-essentially based utility interface call to make your mind up on up attendee names. Whereas the SQLite database downloaded used to be encrypted, one other API call equipped that key.
But any other SQLite database that can perchance soundless be pulled down by the utilize of the utility’s APIs is now no longer encrypted, and it contains more personal data, including names, addresses, cell phone numbers, company names, and social media story hyperlinks. Ars seemed at that database, and it appears to possess easiest dealer and speaker data, so it be seemingly deliberately insecure because it be much less sensitive.
Here is the 2nd time an RSA mobile utility has leaked attendee data. In 2014, an utility built by one other developer, QuickMobile, used to be chanced on by Gunter Ollmann (who used to be that time at IOactive) to own a SQLite database containing personal data on registered attendees.

Commentaires récents