Announcing 1.1.1.1: the quickest, privacy-first user DNS carrier
Cloudflare’s mission is to support invent a better Web. We’re mad this day to purchase one more step toward that mission with the originate of 1.1.1.1 — the Web’s quickest, privacy-first user DNS carrier. This post will talk a shrimp about what that is and loads about why we determined to enact it. (Whenever you are serious in regards to the technical important components on how we built the carrier, review out Ólafur Guðmundsson’s accompanying post.)
Mercurial Primer On DNS
DNS is the directory of the Web. Everytime you click on on a hyperlink, ship an electronic mail, start a mobile app, normally one in all the principle issues that has to happen is your scheme desires to gaze up the take care of of a web based sing material. There are two facets of the DNS network: Authoritative (the sing material side) and Resolver (the user side).
Every enviornment desires to maintain an Authoritative DNS supplier. Cloudflare, since our originate in September 2010, has disappear an extremely speedily and extensively-frail Authoritative DNS carrier. 1.1.1.1 doesn’t (straight) swap something about Cloudflare’s Authoritative DNS carrier.
On the diversified side of the DNS scheme are resolvers. Every scheme that connects to the Web wants a DNS resolver. By default, these resolvers are automatically space by whatever network you are connecting to. So, for most Web users, when they connect with an ISP, or a coffee shop wifi sizzling verbalize, or a mobile network then the network operator will dictate what DNS resolver to employ.
DNS’s Privateness Topic
The scenario is that these DNS companies are incessantly gradual and no longer privacy respecting. What many Web users don’t realize is that even at the same time as you are visiting a web based space that is encrypted — has the shrimp green lock on your browser — that doesn’t support your DNS resolver from shimmering the identity of your complete web sites you discuss with. Meaning, by default, your ISP, every wifi network that it is possible you’ll maintain connected to, and your mobile network supplier maintain a listing of every space that it is possible you’ll maintain visited while the usage of them.
Community operators maintain been licking their chops for some time over the muse of taking their users’ browsing knowledge and discovering a merely about monetize it. In america, that obtained more uncomplicated a twelve months within the past when the Senate voted to effect away with strategies that restricted ISPs from promoting their users’ browsing knowledge. With your complete command over the info that firms take care of Facebook and Google are accumulating on you, it worries us to now add ISPs take care of Comcast, Time Warner, and AT&T to the listing. And, effect no mistake, this is no longer a US-handiest scenario — ISPs around the realm count on the identical privacy-invading different.
DNS’s Censorship Topic
But privacy issues lengthen some distance beyond supreme ad targeting. Cloudflare operates Mission Galileo to present protection to with out payment politically or artistically important organizations around the realm from cyber attack. By the venture we offer protection to groups take care of LGBTQ organizations focused within the Middle East, journalists keeping political corruption in Africa, human rights workers in Asia, and bloggers on the bottom keeping the war in Crimea. We’re in actuality elated with the venture and we’re in actuality handsome at stopping cyber attacks launched at its participants.
But it has been depressing to us to be aware all too normally how DNS could maybe very properly be frail as a scheme of censorship in opposition to many of the groups we offer protection to. Whereas we’re handsome at stopping cyber attacks, if a user’s DNS gets blocked there might be been nothing we could maybe enact to support.

In March 2014, as an illustration, the govt. of Turkey blocked Twitter after recordings exhibiting a govt corruption scandal leaked on-line. The Web used to be censored by the country’s ISP’s DNS resolvers blocking DNS requests for twitter.com. Of us literally spray painted eight.eight.eight.eight, the IP of Google’s DNS resolver carrier, on walls to support fellow Turks obtain support on-line. Google’s DNS resolver is gorgeous, but vary is handsome and we view we could maybe enact even better.
Building a Particular person DNS Carrier
The insecurity of the DNS infrastructure struck the crew at Cloudflare as a computer virus at the core of the Web, so we space out to enact something about it. Given we disappear one in all the ideally gracious, most interconnected global networks — and maintain rather just a few journey with DNS — we maintain been properly positioned to originate a user DNS carrier. We began sorting out and positioned that a resolver, running all the way thru our global network, outperformed any of the diversified user DNS companies available (along with Google’s eight.eight.eight.eight). That used to be encouraging.
We began talking with browser manufacturers about what they’d desire from a DNS resolver. One notice saved coming up: privacy. Previous supreme a dedication to no longer employ browsing knowledge to support target ads, they wished to effect sure that we would maybe wipe all transaction logs inner a week. That used to be a easy request. If truth be told, we knew we could maybe drag a lot extra. We dedicated to by no methodology writing the querying IP addresses to disk and wiping all logs inner 24 hours.
Cloudflare’s enterprise has by no methodology been built around monitoring users or promoting promoting. We don’t count on private knowledge as an asset; we count on it as a toxic asset. Whereas we desire some logging to pause abuse and debug issues, we couldn’t imagine any scenario where we would want that knowledge longer than 24 hours. And we wished to place our money where our mouth used to be, so we dedicated to preserving KPMG, the properly-respected auditing firm, to audit our code and practices yearly and publish a public document confirming we’re doing what we mentioned we would.
Enter 1.1.1.1

The one component that used to be left used to be we wished a pair of memorable IPs. Undoubtedly one of many core causes for the DNS scheme is that IPs aren’t very memorable. 172.217.10.forty six is no longer almost as memorable as Google.com. But DNS resolvers inherently can’t employ a catchy enviornment on fable of they are what must be queried in uncover to decide out the IP take care of of a web based sing material. Or no longer it is a rooster and egg scenario. And, if we wished the carrier to be of support in occasions of crisis take care of the tried Turkish coup, we wished something easy passable to preserve in thoughts and spraypaint on walls.
We reached out to the crew at APNIC. APNIC is a Regional Web Registery (RIR) guilty for handing out IPs within the Asia Pacific situation. It is one in all 5 RIRs that arrange IP allocation globally, the diversified four being: ARIN (North The United States), RIPE (Europe/Middle East), AFRINIC (Africa), and LATNIC (South The United States).
APNIC’s study community held the IP addresses 1.1.1.1 and 1.0.0.1. Whereas the addresses maintain been gracious, so many folks had entered them into assorted random systems that they maintain been continuously overwhelmed by a flood of rubbish traffic. APNIC wished to view this rubbish traffic but any time they’d tried to order the IPs, the flood would overwhelm any dilapidated network.
We talked to the APNIC crew about how we wished to effect a privacy-first, extremely speedily DNS scheme. They view it used to be a laudable purpose. We equipped Cloudflare’s network to receive and review the rubbish traffic in swap for being in a position to present a DNS resolver on the memorable IPs. And, with that, 1.1.1.1 used to be born.
Severely, April 1?
The most handy demand that remained used to be when to originate the original carrier? Here’s the principle user product Cloudflare has ever launched, so we wished to succeed in a wider viewers. On the identical time, we’re geeks at coronary heart. 1.1.1.1 has four 1s. So it looked clear that four/1 (April 1st) used to be the date we wished to originate it.
Never thoughts that it used to be a Sunday. Never thoughts that it used to be on Easter and all thru Passover. Never thoughts that it used to be April Fools Day — a day where tech firms normally inch out fictional companies they mediate are cute while the media and the comfort of the non-tech world collectively roll their eyes.
We justified it to ourselves that Gmail, one more fine, non-fictional user carrier, also launched on April 1, 2004. Needless to disclose, as Cloudflare’s PR crew has normally pointed out to me within the disappear as a lot as originate, the Gmail originate day used to be a Thursday and no longer on Easter. Nearly every media briefing I did this week before the originate the reporter made me content that this wasn’t a comical epic. And it is no longer. I content. And essentially the most moving merely about demonstrate that is drag to 1.1.1.1, be aware the instructions to space it up, and count on for yourself. Or no longer it is accurate. And it is suited.
Why Did We Rep It?
The reply to why we built the carrier goes support to our mission: to support invent a better Web. Of us merely about work at Cloudflare each day in uncover to effect the Web better, extra stable, extra legit, and extra atmosphere superior. It sounds tacky, but it actually’s factual.
When, in 2014, we determined to permit encryption with out cost for all our potentialities rather just a few of us externally view we maintain been loopy. Along with to the technical and monetary costs, SSL used to be, at the time, the principle incompatibility between our free and paid carrier. And but, it used to be a laborious technical scenario, and clearly the merely component to enact for the Web, so we did it. And, in a single day, we doubled the scale of the encrypted web. I’m elated with the undeniable fact that, three and a half of years later, the comfort of the industry is beginning to be aware swimsuit. The obtain need to maintain been encrypted from the starting place. Or no longer it is a computer virus it wasn’t. We’re doing what we can enact fix it.
When, final twelve months, we made DDoS mitigation free and unmetered all the way thru all our plans rather just a few of us but again scratched their heads. But it used to be the merely component to enact. You don’t need to maintain a enormous checking fable to face as a lot as hackers and bullies on-line. Over time we’re convinced that DDoS mitigation will be a commodity included with all platforms, so after all we could maybe peaceful be leading the merely about obtain to that inevitable that discontinuance.
Section of the explanation now we maintain been in a position to hire the form of fine crew is that we purchase on sizable challenges take care of this when they’re the merely component to enact. Stroll around the govt. center and our crew’s laptops are embellished with 1.1.1.1 stickers on fable of we’re all elated with what we’re doing. That by myself made constructing this a no brainer. (PS – Sound fun? We’re hiring.)

In direction of a Better DNS Infrastructure
But there might be extra. DNS itself is a 35-twelve months-veteran protocol and it is exhibiting its age. It used to be by no methodology designed with privacy or security in thoughts. In our conversations with browser, working scheme, app, and router manufacturers almost everybody lamented that, even with a privacy-first carrier take care of 1.1.1.1, DNS inherently is unencrypted so it leaks knowledge to any individual who’s monitoring your network connection. Whereas that is extra difficult to tune for somebody take care of your ISP than if they disappear the DNS resolver themselves, it is peaceful no longer stable.
What’s wished is a switch to a brand original, smartly-liked protocol. There are a pair of diversified approaches. One is DNS-over-TLS. That takes the current DNS protocol and adds transport layer encryption. Yet another is DNS-over-HTTPS. It includes security but also your complete smartly-liked enhancements take care of supporting diversified transport layers (e.g., QUIC) and original applied sciences take care of server HTTP/2 Server Push. Every DNS-over-TLS and DNS-over-HTTPS are start requirements. And, at originate, now we maintain ensured 1.1.1.1 supports each and each.
We mediate DNS-over-HTTPS is extremely promising — speedily, more uncomplicated to parse, and encrypted. To this point, Google used to be essentially the most handy scale supplier supporting DNS-over-HTTPS. For obvious causes, on the opposite hand, non-Chrome browsers and non-Android working systems maintain been reluctant to invent a carrier that sends knowledge to a competitor. We’re hoping that with an fair DNS-over-HTTPS carrier now available, we will count on extra experiments from browsers, working systems, routers, and apps to present a boost to the protocol.
We aren’t looking out out for any must be essentially the most handy such carrier. Extra vary in DNS suppliers is a Correct Thing™. If, over time, a sturdy ecosystem of networks offering DNS-over-HTTPS give a boost to develops then that’ll drag down as one in the entirety we will be elated with in furthering our mission to support invent a better Web.
Tying It All Together
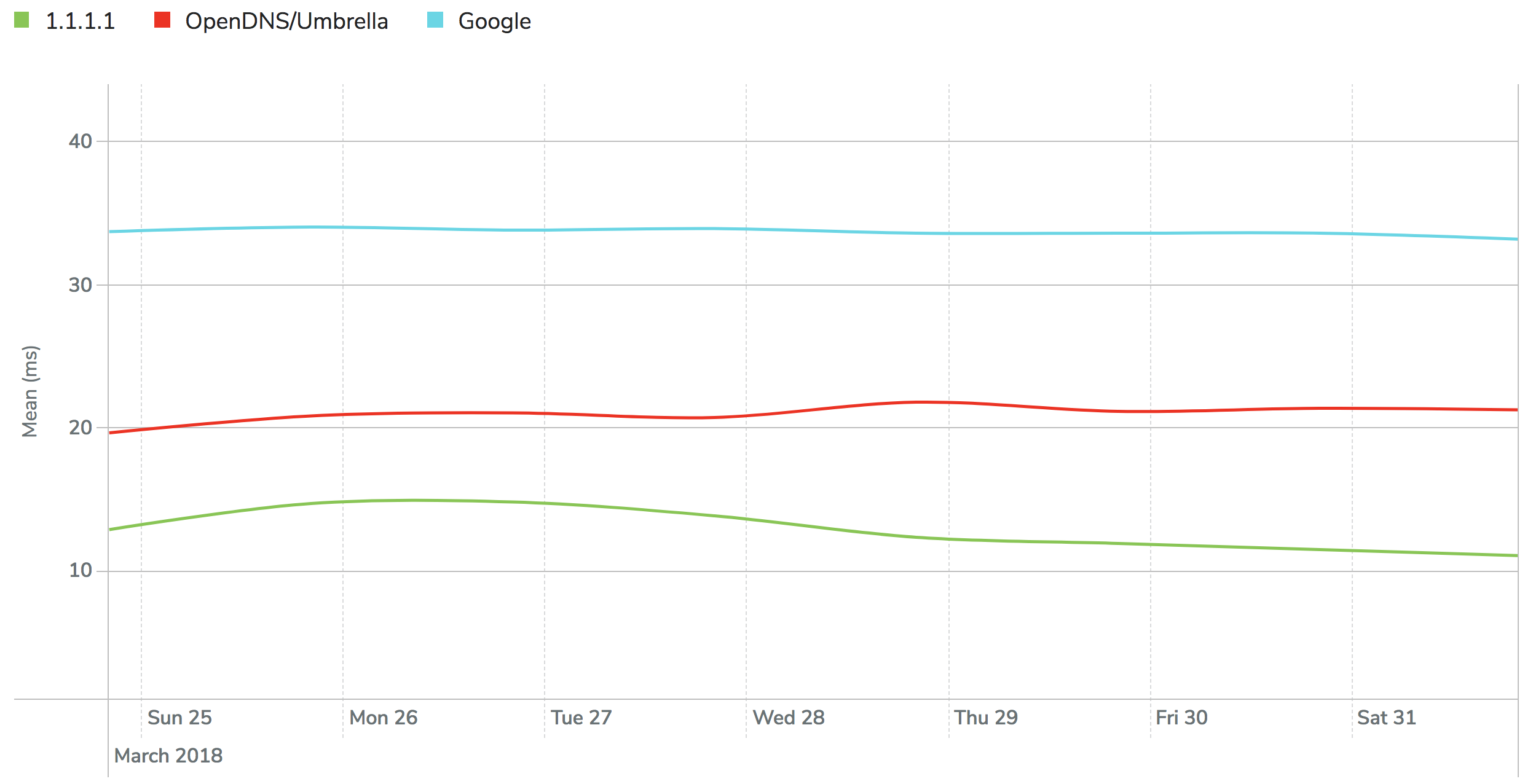
Whereas DNSPerf now ranks 1.1.1.1 as the quickest DNS resolver when querying non-Cloudflare potentialities (averaging around 14ms globally), there might be an added support at the same time as you are a Cloudflare customer the usage of our Authoritative DNS. Since the resolver and the recursor are in actuality on the identical network, running on the identical hardware, we can solution queries for Cloudflare’s potentialities incredibly quick. We could maybe moreover give a boost to rapid updates, with out having to reside up for TTLs to expire.
In diversified words, every original particular person of 1.1.1.1 makes Cloudflare’s Authoritative DNS carrier a shrimp better. And, vice versa, every original particular person of Cloudflare’s Authoritative DNS carrier makes 1.1.1.1 a shrimp better. So, at the same time as you are an current Cloudflare customer, support your users to envision out 1.1.1.1 and likewise you will count on performance benefits from all of us that enact.
Take a look at with https://1.1.1.1/ from any scheme to originate with the Web’s quickest, privacy-first DNS carrier.
Be taught Extra

Commentaires récents