How your ethereum might perchance per chance also also be stolen through DNS rebinding

With the original buzz around exploiting unauthenticated JSON-RPC products and services on localhost ignited by Tavis Ormandy, The very very first thing that came to my mind used to be ethereum shoppers(Geth, Mist and Parity).
Most of the ethereum shoppers flee a JSON-RPC service on port 8545 on localhost, but because it’s on localhost, we are in a position to’t uncover admission to it without delay from user’s browser due to the SOP.
This command within the electrum wallet exploited the CORS headers to select out adjust over the user’s electrum wallet through JSON-RPC on localhost.
Geth’s JSON-RPC appeared pretty salvage as it didn’t return any CORS header, but then cpacia commented something on the half of-patch of the electrum wallet which sparked my hobby. Listed below are the actual phrases
Correct disabling CORS is still at possibility of a DNS rebinding attack. It beget to be authenticated. ~ cpacia
I had heard about DNS rebinding but by no methodology tried to look into it powerful. Since Geth’s JSON-RPC shall be unauthenticated, it might perchance also be at possibility of DNS rebinding attacks too?
Right here is frequent definition of DNS rebinding.
I started taking a look into DNS Rebinding, but your whole articles had been basically pretty long-established. Then I asked about it in Bug Bounty Forum and Luke Young linked me his superior Defcon talk about favorite DNS rebinding exploitation. It also included an computerized machine to acquire DNS rebinding achievable on various the favored browsers.
Nonetheless I was more outlandish and I didn’t must make use of any pre-made machine, So I started writing my contain DNS server. Python has a reasonably good library called dnslib which dealt with various the stuff for me. I registered a enviornment, setup some glue records pointing towards my server and passe them as the nameservers.
I needed to survey how varied browsers behaved with very low TTLs, so I made my DNS server return TTLs < 5. Chrome, Firefox and Safari cached the DNS responses for 60 seconds, although the TTL used to be no longer up to 5.
60 seconds isn’t such a truly very prolonged time, and I reflect I will acquire a user end on my webpage for a minimal of 60 seconds. Now the solely thing left used to be to in actuality strive it.
I ran geth with the --rpc flag(in testnet of-route)
geth –rpc –testnet
Now used to be the time for some javascript, and this used to be the toughest fragment. I’m no longer a appropriate web-dev and it used to be pretty animated for me to wrap my head around the every time Javascript behaviour. I hacked together a reasonably wrong but working javascript in Three hours. The preliminary outcomes had been a success.
Now to acquire it work with geth, I had to flee my web server and enviornment on port 8545 as SOP also follows the port. Nonetheless this might perchance look kinda sketchy if I sent the hyperlink to any individual with port 8545 in it.
The answer used to be iframes. I made apache hear on each 8545 and Eighty, and organize a virtual host for every port. Now I could perchance per chance also iframe the port 8545 and flee your whole javascript within the hidden iframe.
One more command used to be about more than one users, what if more than one users on the identical time visited my enviornment? The DNS server would uncover puzzled as I was the utilization of a counter basically based solely mostly machine and there used to be no manner to divulge apart between requests from person users. This had me stumped for a whereas except I remembered subdomains.
I could perchance per chance also iframe a random subdomain every time a user visits the predominant enviornment and use it as an identification. I do know I could perchance per chance also no longer be explaining it well but right here’s an instance.
Let’s preserve that my enviornment is attacker.com and my server’s IP is 87.87.87.87 Right here is how the circulate goes.
- The victim opens
attacker.comin his browser. - First, a DNS query for
attacker.comis disbursed to my server and it responds with the actual IP87.87.87.87 - Next,
attacker.comis loaded into the user’s browser, which then creates a hidden iframe with a random subdomainrandomrsub.attacker.com:8545and appends it to the body - Now, a DNS query is disbursed to my server for the subdomain
randomrsub.attacker.com, and the DNS server again responds with the actual IP87.87.87.87. Nonetheless this time, because it’s on port 8545, the apache responds with a particular virtual host, which begins the DNS rebinding. - The javascript on
randomrsub.attacker.com:8545waits 60 seconds, after which sends an XmlHttpRequest torandomrr.attacker.com:8545/test. - For the reason that DNS cache has expired, the browser resolves the DNS again. This time, my server responds with an IP of
127.Zero.Zero.1. - Now the query is with out a doubt sent to
127.Zero.Zero.1:8545/testas an different of my server, and because it’s beneath the muse ofrandomrr.attacker.com:8545, we are in a plot to learn the response. - Since we are producing a random subdomain everytime, we are in a position to now even accommodate more than one users as the subdomain can act their identification token.
I also had to optimize the javascript a minute bit to verify it truly works ninety five% of the time. I added some spurious DNS lookups earlier than the actual ones so that it doesn’t reply with the atrocious IP on the atrocious time.
This might perchance per chance also most incessantly be exploited with a kept XSS too. Correct point a script src to the js file which adds the iframe and TADA!!
So now we are in a position to learn responses from JSON-RPC service, which methodology we are in a position to learn their ethereum addresses, their balance and doubtlessly preserve their ether if their story is unlocked. The JSON-RPC API has pretty decent manner called eth_sendTransaction which is in a plot to be most incessantly passe to send ethereum from the user’s story.
I the truth is beget organize a Proof-of-Concept on http://rebinddns.ml. Must you end on it for better than 60 seconds and likewise you’re working Geth(or every other ethereum client) with JSON-RPC, you might perchance perchance per chance take into story an alert() which is in a plot to beget your ethereum addresses and their balance.
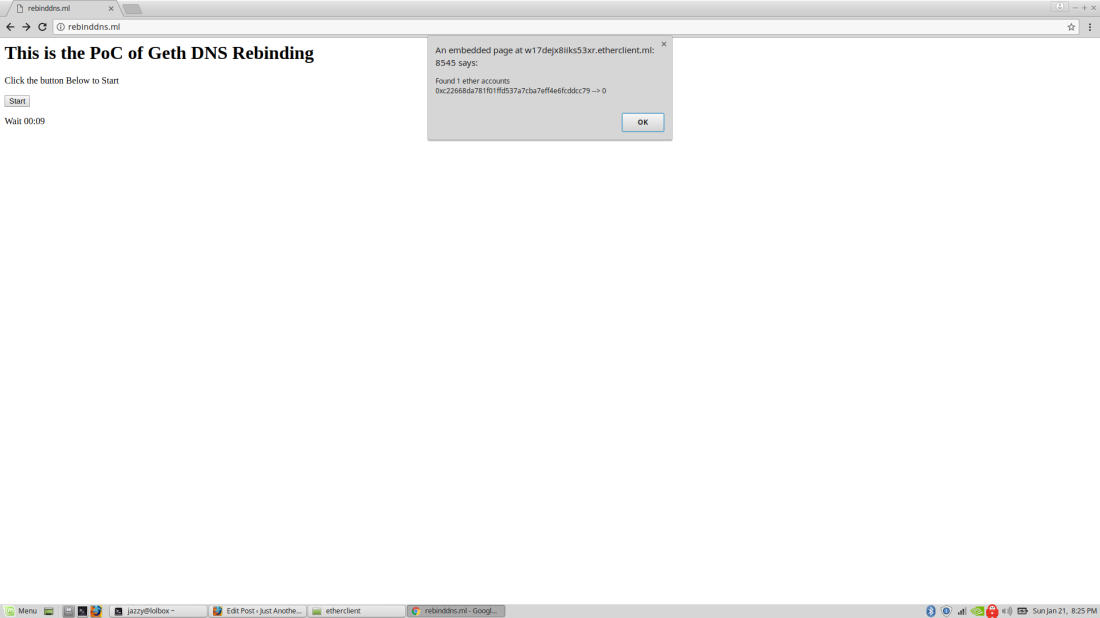
All of the files passe within the PoC might perchance per chance also also be found on my github.
-
min.js– The Js file which generates a hidden iframe of a subdomain on port 8545 -
major.js– The Js file which executes the DNS Rebinding -
server.py– The DNS server written in python
I the truth is beget verified that Geth, the C++ ethereum client and the python client are susceptible. The PoC has been tested on Firefox, Chrome and Safari.
PS: This has been reported to the ethereum basis but they don’t select into consideration it a legit vulnerability.
For any questions, which you might perchance well perchance hit me up on my twitter @ret2got
Read More

Commentaires récents