Flight Sim Firm Embeds Malware to Capture Pirates’ Passwords – TorrentFreak

Flight sim company FlightSimLabs has stumbled on itself in agonize after placing in malware onto users’ machines as an anti-piracy measure. Code embedded in its A320-X module contained a mechanism for detecting ‘pirate’ serial numbers dispensed on The Pirate Bay, which then precipitated a path of by which the company stole usernames and passwords from users’ web browsers.
 Anti-piracy systems and DRM come in all shapes and sizes, none of them particularly current, nonetheless one deployed by flight sim company FlightSimLabs is at possibility of creep down in history as no doubt a few of the contaminated.
Anti-piracy systems and DRM come in all shapes and sizes, none of them particularly current, nonetheless one deployed by flight sim company FlightSimLabs is at possibility of creep down in history as no doubt a few of the contaminated.
It started the day gone by on Reddit when Flight Sim client ‘crankyrecursion’ reported moderately further one thing in his download of FlightSimLabs’ A320X module.
“Using file ‘FSLabs_A320X_P3D_v2.zero.1.231.exe’ there appears to be a file called ‘test.exe’ incorporated,” crankyrecursion wrote.
“This .exe file is from http://securityxploded.com and is touted as a ‘Chrome Password Dump’ instrument, which appears to work – particularly because the installer would usually flee with Administrative rights (UAC prompts) on Home windows Vista and above. Can anyone shed gentle on why this instrument is incorporated in a supposedly trusted installer?”
The existence of a Chrome password dumping instrument is no longer any doubt trigger for terror, especially if the tool had been got from a less-than-worthy provide, similar to a torrent or an identical predicament, given the functionality for zero.33-birthday party air pollution.
On the other hand, with the seemingly for a putrid zero.33-birthday party dumping one thing nasty in a pirate launch aloof lurking on the horizon, issues took an surprising turn. FlightSimLabs chief Lefteris Kalamaras made an announcement usually admitting that his company modified into once in the support of the malware installation.
“We had been made mindful there might maybe be a Reddit thread started tonight concerning our most well liked installer and how a instrument is incorporated in it, that indiscriminately dumps Chrome passwords. That is no longer any longer correct form knowledge – in point of fact, the Reddit thread modified into once posted by an individual who’s no longer any longer our customer and has one way or the other got our installer with out shopping,” Kalamaras wrote.
“[T]here must no longer any instruments ragged to exhibit any snug knowledge of any customer who has legitimately purchased our products. All of us keep in mind that you just place a host of belief in our products and this will seemingly be opposite to what we mediate.
“There might maybe be a particular manner ragged against specific serial numbers that had been identified as pirate copies and had been making the rounds on ThePirateBay, RuTracker and assorted such malicious sites,” he added.
In a nutshell, FlightSimLabs place in a password dumper onto ALL users’ machines, whether they had been pirates or no longer, nonetheless then fully activated the password-stealing module when it sure that individual ‘pirate’ serial numbers had been ragged which matched these on FlightSimLabs’ servers.
“Test.exe is share of the DRM and is fully centered against specific pirate copies of copyrighted tool got illegally. That program is fully extracted like a flash and is no longer any longer in point of fact below any conditions ragged in reputable copies of the product,” Kalamaras added.
That didn’t provoke Luke Gorman, who published an prognosis slamming the flight sim company for knowingly placing in password-stealing malware on users machines, even these that purchased the title legitimately.
Password stealer in motion (credit ranking: Luke Gorman)
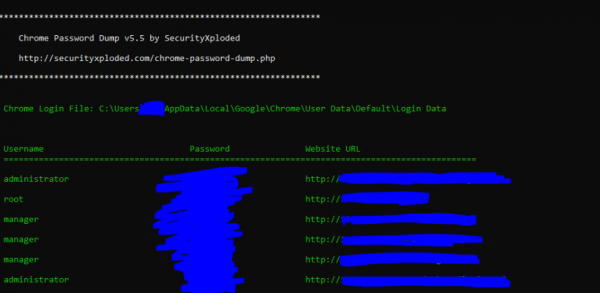
Making issues even worse, the FlightSimLabs chief went on to advise that knowledge being got from pirates’ machines in this form is at possibility of be ragged in courtroom or assorted approved processes.
“This form has already successfully supplied knowledge that we’re going to teach in our ongoing approved battles against such criminals,” Kalamaras revealed.
Whereas the teach of the extracted passwords and usernames in assorted places will remain to be seen, it appears that FlightSimLabs has had a alternate of coronary heart. With quick carry out, the company is pointing clients to a sleek installer that doesn’t encompass code for stealing their most snug knowledge.
“I must reiterate and reaffirm that we as an organization and as flight simmers would never attain the relaxation to knowingly violate the belief that you just are going to dangle gotten positioned in us by no longer fully trying to search out our products nonetheless supporting them and FlightSimLabs,” Kalamaras acknowledged in an substitute.
“Whereas the majority of our clients keep in mind that the fight against piracy is a cosmopolitan and ongoing battle that usually requires drastic measures, we keep in mind that about a of you had been sad with this specific manner which is at possibility of be regarded as as to be slightly heavy handed on our share. It is for this cause we now dangle got uploaded an as much as this point installer that does no longer encompass the DRM overview file in ask.”
Additional prognosis of the ‘DRM’ has been published by Fidus.
Change Feb 20: FlightSimLabs has issued every other converse, this time distinguished extra detailed, which explains that the company modified into once targeting a particular cracker of their video games.
“Flash support to our first A320-X launch for FSX / P3Dv3 (32bit) – we stumbled on quickly after the launch of our product for these simulator variations that there had been specific crackers who had been winning in sidetracking our protection draw by the usage of offline serial number generators.
We would maybe no longer get how this might maybe maybe occur, nonetheless we came about upon a particular blueprint of knowledge (username / e mail / serial number) that would maybe per chance occur commonly from specific IP addresses.
We tried to add extra assessments in our subsequent installer releases, nonetheless the explicit crackers had been additionally upping their game in ensuring they sidetracked our installer. We even went so a long way as to determine precisely who the cracker modified into once (we now dangle got his name accessible upon seek knowledge from of any authorities), nonetheless unfortunately we would no longer be ready to enter the registration-fully websites he modified into once the usage of to provide this knowledge to assorted pirates.
We stumbled on through the IP addresses tracked that the actual cracker had ragged Chrome to contact our servers so we made up our minds to care for his knowledge straight – and ONLY his knowledge (obviously, we perceive now that of us got very upset about this – we’re very sorry once more!) as we had a in point of fact correct thought of what serial number the cracker ragged in his efforts.”
Learn More

Commentaires récents