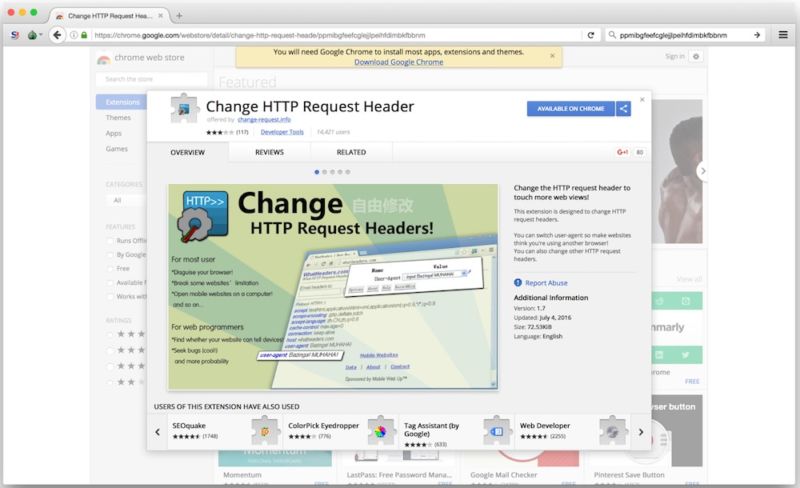
Researchers grasp uncovered four malicious extensions with extra than 500,000 mixed downloads from the Google Chrome Web Store, a discovering that highlights a key weak point in what’s broadly belief of to be the Web’s most stable browser. Google has since eliminated the extensions.
Researchers from security company ICEBRG chanced on the get after detecting a suspicious spike in outbound network visitors coming from a customer workstation. They rapidly learned it used to be generated by a Chrome extension called HTTP Ask Header as it feeble the infected machine to surreptitiously plod to promoting-associated Web hyperlinks. The researchers later learned three loads of Chrome extensions—Nyoogle, Stickies, and Lite Bookmarks—that did mighty the same thing. ICEBRG suspects the extensions were portion of a click on-fraud scam that generated earnings from per-click on rewards. However the researchers warned that the malicious add-ons could per chance merely as simply grasp been feeble to seek for on the folk or organizations who installed them.
« On this case, the inherent have faith of zero.33-birthday celebration Google extensions, and accredited possibility of user withhold watch over over these extensions, allowed an expansive fraud marketing campaign to be triumphant, » ICEBRG researchers wrote in a file published Friday. « Within the fingers of a cultured threat actor, the same tool and intention could grasp enabled a beachhead into target networks. »
Google eliminated the extensions from its Chrome Web Store after ICEBRG privately reported its findings. ICEBRG moreover alerted the Nationwide Cyber Security Centre of the Netherlands and the US CERT. In its public file, ICEBRG went on to present how the how the malicious extensions worked:
By develop, Chrome’s JavaScript engine evaluates (executes) JavaScript code contained within JSON. Attributable to security concerns, Chrome prevents the capability to retrieve JSON from an external source by extensions, which have to explicitly ask its use via the Yell Security Policy (CSP). When an extension does enable the ‘unsafe-eval’ (Resolve 3) permission to originate such actions, it could truly per chance retrieve and process JSON from an externally-managed server. This creates a pronounce in which the extension author could per chance inject and enact arbitrary JavaScript code anytime the replace server receives a ask.
The Exchange HTTP Ask Header extension downloads JSON via a function called ‘update_presets()’ which downloads a JSON blob from ‘exchange-ask[.]records’
Right here’s by no intention the main time Chrome extensions grasp been abused. In tiresome July and early August, unknown attackers compromised the accounts of no longer no longer up to two Chrome extension developers. The criminals then feeble their unauthorized net right of entry to to automatically install extension updates that injected adverts into the websites customers visited. Later in August, Renato Marinho, who’s the Chief Study Officer of Morphus Labs and a volunteer at the SANS Institute, uncovered an present an explanation for financial institution-fraud scam that feeble a malicious extension in Google’s Chrome Web Store to save end targets’ passwords.
Chrome is broadly belief of most certainly the most Web’s most stable browsers, in monumental portion thanks to the like a flash availability of security patches and the effectiveness of its security sandbox, which prevents untrusted yell material from interacting with key parts of the underlying working method. Undermining that security is the threat posed by malicious extensions. Of us ought to withhold away from putting in them except the extensions present a trusty profit, after which only after careful learn into the developer or evaluation of the extension code and habits.

Commentaires récents